Published on: May 12, 2022
Vendor Risk Management: Understanding The Foundations & Benefits
Outsourcing has become a popular business strategy to help organizations save money and optimize operational efficiency. However, since vendors often have access to critical systems and data, using third parties introduces risks that can lead to severe damage to your organization if not properly managed.
Here is where Vendor Risk Management (VRM) comes in.
This article is part one of a three-part guide that will help you understand the following areas:
Vendor Risk Management foundations
Critical risks you must know to protect your organization
How and when to assess vendors
How to implement a Vendor Risk Management Program, and
In-depth exploration of the vendor lifecycle
In part one, you'll learn everything about the foundations of VRM, from key definitions, types of risks your organization might be facing, how to manage the vendor ecosystem to the benefits of an effective VRM.
Let's begin!
Traditional vs Enterprise Risk Management
A good idea would be to define these two popular concepts. Traditional Risk Management (TRM) is defined as an organization's earliest form of risk management that addresses loss exposures generated by financial, operational, and credit risks. It is a reactive approach that seeks solutions when problems surface.
However, this siloed approach and its limited scope on financial hazards make it challenging for organizations to proactively anticipate new risks and make informed decisions at the strategic organizational level.
On the other hand, Enterprise Risk Management is a more holistic and strategic evolutionary approach to risk management. It's a program developed by the Committee of Sponsoring Organizations of the Treadway Commission (COSO) in 2004, that aims to anticipate potential opportunities and threats affecting an organization and make decisions at the top management level.
It also encompasses a broader range of potential risks, including strategic, business, operational, financial, reputational, and regulatory risks. ERM integrates risk management principles with business strategy to drive performance more effectively.
Vendor Risk Management is a critical component of ERM, allowing organizations to identify and mitigate risks associated with their vendors and third-party service providers.
The main reasons why Vendor Risk Management is vital include the following:
Emerging privacy regulations that make data controllers and processors responsible for the entire data flow.
Infosec standards that mandate vendor assessment.
Interconnected systems (DevOps, infrastructure).
Resilience becoming a hot topic.
Vendor Risk Management helps organizations ensure that their vendors are adhering to the same data protection and security standards as the organization itself, thus reducing the risk of data breaches and other security incidents.
Third-Party Risk, Vendor Risk, Supplier Risk, Service Provider Risk - What's the Difference?
Organizations may use different terminology in vendor risk management to describe their vendors. Using vendors interchangeably with other terms such as third party, supplier, or service provider can get confusing as these terms look all the same from a quick glance. However, there are subtle differences between these terms.
Before diving into the differences, let's start with where they are the same. Third-Party Risk Management (TPRM), Vendor Risk Management (VRM), and Supplier Risk Management (SRM) are programs that organizations employ to manage their relationships and risks associated with external parties. The purpose of the programs is the same " identify, assess, manage, and mitigate risks concerning external parties.
Now, let's check out the differences. Slight variations arise in the nature of the relationship and resources provided by them.
Third-Party Risk Management (TPRM) is a generic catch-all term used to describe the management of risks from all third parties with which an organization interacts or does business with. This would include various external parties which fall into different categories, such as business partners, service providers, suppliers, vendors, customers, even government agencies, and not-for-profit entities, to name a few.
In essence, TPRM is the overarching umbrella that covers all types of risk management activities associated with each external party with which the organization has a business relationship.
In contrast, Vendor Risk Management (VRM), Supplier Risk Management (SRM), and Supplier Provider Risk Management are narrower in scope and used to describe the risk activities associated with a service or product provider.
Supplier Risk Management (SRM) focuses on a vendor's processes, policies, and financial health to determine their risk level and supply chain workflow.

What's the Big Deal About Vendor Risk Management?
In recent years, outsourcing has become a necessary business component in a highly connected world. Engaging third-party subject matter experts to provide these services can lead to cost savings, a wealth of expertise not currently available in-house, and stronger performance results.
A company can launch, expand or scale its business quickly without requiring a massive investment to build the infrastructure from the ground up. Whether hiring contractors or launching a new solution or technology, many vendors can support these initiatives.
On the flip side, the vendor relationship also presents more significant risk and uncertainty to the organization. There is a dependency on the vendors to provide a crucial function, both reliably and consistently.
Unfortunately, any service disruptions to the vendor's operations can lead to a domino effect that can potentially affect millions of businesses or customers.
Recent global events such as the COVID-19 pandemic, supply chain blockage of the Suez Canal, rising energy prices from the Ukraine-Russia war, or cybersecurity attacks on international vendors (such as Colonial Pipeline, JBS Foods, Kaseya and SolarWinds) have amplified the crippling effects of vendor disruptions. No business is immune, regardless of the organization's size, industry, or geographic location.
Implementing an effective vendor risk management (VRM) program can minimize the harmful impacts of these events and reduce an organization's overall risk exposure from third-party services.
More importantly, Vendor Risk Management has also become a legal requirement. For example, the GDPR requires organizations to conduct risk assessments to identify internal risks and with third parties that will manage personal data.
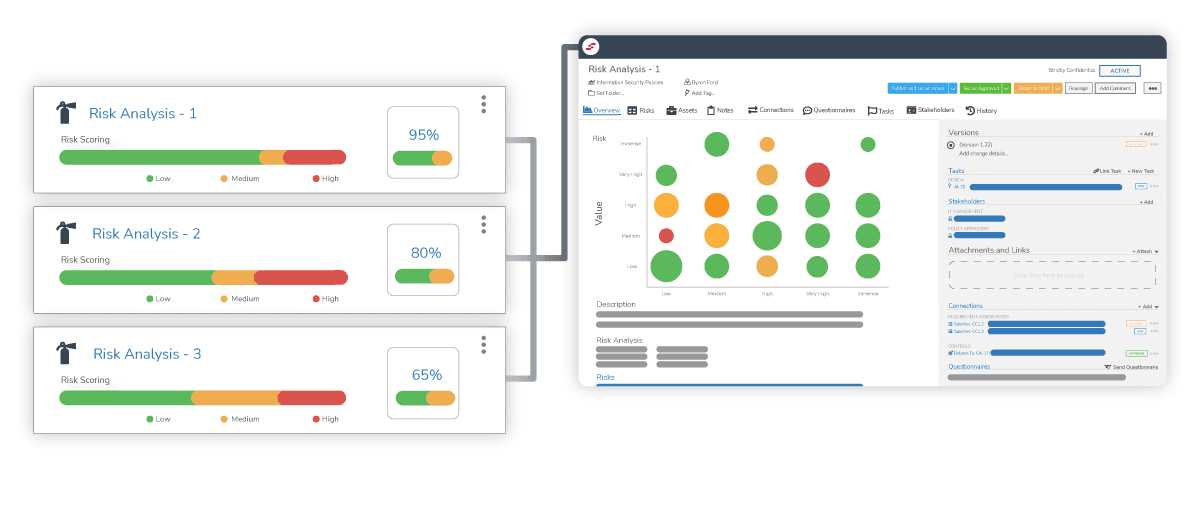
The Risks Vendors can Introduce Into Your Organization
Vendors are an extension of your business, which means an organization is ultimately liable for consequences resulting from business failures, service disruptions, or security breaches.
Having a thorough understanding of the different types of vendor risks will help you to classify vendors based on their potential threat to the business and minimize the magnitude of reputational damage from adverse events.
When designing a VRM program, the question arises as to what aspects of the vendor relationship to focus on. Since assessing every risk is unrealistic, taking a risk-based approach and focusing your attention on common vendor risks is a good starting point.
The following are some of the top risks that are important for you to monitor:
Compliance and regulatory risk: A vendor violates laws or regulations that you're obligated to follow. Depending on your industry and the services offered, the business may be required to comply with privacy, data protection, financial or environmental regulations. A failure to maintain compliance can result in harsh fines and enforcement actions against the business.
Cybersecurity risk: Vendors may be susceptible to data breaches, malware, ransomware, and other cyber-attacks. The increasing sophistication and volume of cyber threats on vendors make monitoring a vendor's cybersecurity posture more critical than ever.
Financial risk: Your organization could miss its financial performance goals when a vendor fails to deliver on requirements or high vendor costs are not adequately addressed.
Operational risk: A vendor's failure to deliver the services or goods as promised could lead to the organization's inability to carry out subsequent activities. Resilience is essential to operational risk management because it ensures that an organization can continue to deliver critical operations despite disruptions.
Reputational risk: Your organization's public perception and brand could be jeopardized if the vendor you're doing business with is operating in a manner that is inconsistent with the organization's core values or standards.
Strategic risk: When a vendor makes business decisions that are not aligned with your organization's strategic direction, it could impede your ability to capitalize on evolving market trends and business transformation.
The bottom line?
The type of risk a vendor poses to your business will be different, depending on the nature of the business relationship and the services provided. For instance, compliance and regulatory risk will be more significant to a healthcare service provider with access to customer personal health information (PHI) than a supplier who sources office equipment for your business.
In contrast, the supplier would pose a higher likelihood of operational risks from the non-delivery of products due to supply chain disruptions.
Taking a risk-based approach is vital.
Why is this?
Because risks are inherent to every business and cannot be entirely avoided. Accurately assessing "what" risks are applicable to "which" vendors will allow the organization to make informed decisions about the vendor and implement remediation strategies to reduce vendor risks to an acceptable level.
Benefits of an Effective Vendor Risk Management Program
Implementing a VRM program will help effectively manage the sheer volume of vendors and associated risks systematically and transparently. With a robust VRM program, you will control every aspect of the vendor relationship. The program will provide valuable insights to simplify and scale your risk management process. Even though there is no one-size-fits-all approach, key benefits include the following:
Enhance day-to-day operational efficiencies by streamlining and automating key functionalities.
Minimize adverse business disruptions by mitigating critical vendor risks before they become a threat.
Enforce accountability by monitoring performance against contractual obligations.
Control costs by identifying vendor redundancies and addressing overspending.
Monitor vendor adherence to industry standards or regulations.
Who Should be Assessing Their Vendors and When?
Any organization that uses vendors will benefit from implementing a VRM program. Vendor assessments can take place during any stage of the lifecycle - from initial scoping of potential vendors to continuous monitoring activities of existing vendors.
Phase 1 (Procurement):
Every vendor, no matter its size or type of services to be provided, should be evaluated before entering into a partnership (you don't onboard a vendor anymore if they don't pass a privacy assessment).
The due diligence activities will vary depending on the vendor's criticality for the service delivery. For example, IaaS vendors are critical for any SaaS company. Critical for SaaS service delivery.
Another factor influencing the assessment rigor is the type of services being provided and the level of vendor access to your "crown jewels". A vendor with access to corporate strategies or regulated customer data (such as PII or PHI) will warrant a thorough analysis of their cybersecurity controls than a vendor who does not have access.
Phase 2 (Continuous Monitoring during Vendor Lifecycle):
This phase is an essential strategic aspect of a robust VRM program. Implementing a governance capability to track vendor performance in real-time in a dynamic environment will enable more effective decision-making and raise awareness of emerging threats.
Suppose your business runs in a regulated industry or provides service to a specific group of customers. In that case, regulators in your respective jurisdictions will have mandates to evaluate and monitor vendors throughout the lifecycle of the relationship (GDPR, HIPAA, HITRUST, CCPA).
Suppose you are a service provider operating in an unregulated sector and undergo an annual certification to validate control effectiveness. In that case, there is a requirement to assess potential new vendors and evaluate the performance of existing vendors on a yearly basis (SOC 2, ISO27001).
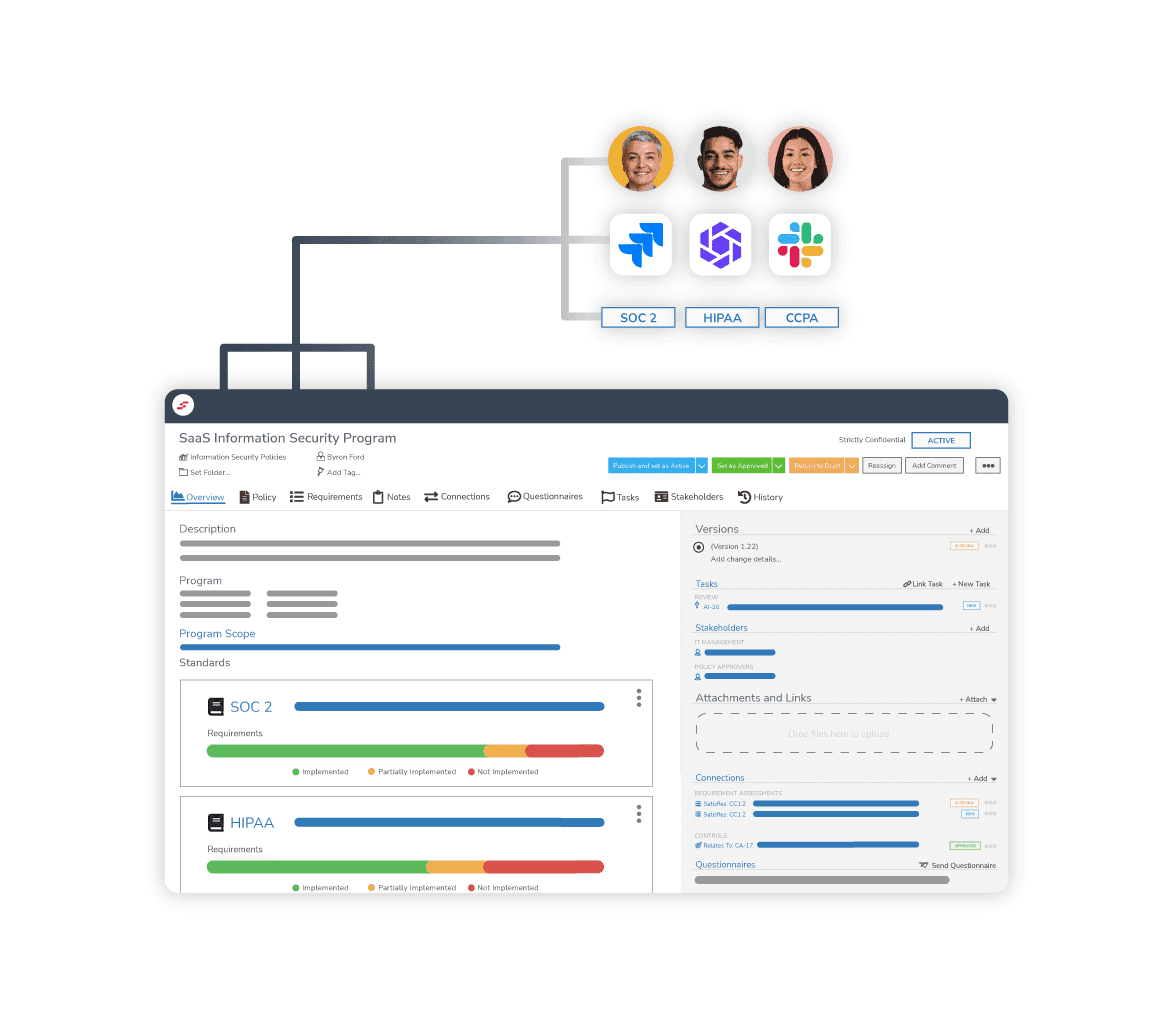
Managing the Vendor Ecosystem
To ensure that vendors are performing following standards and regulatory requirements, organizations have several resources available to manage the vendor ecosystem. The following are some common practices and guidelines that serve a critical role in VRM:
Pre-contractual diligence: Request for Information (RFI), Request for Proposal (RFP), or Request for Quote (RFQ) are used to obtain information about the vendor's goods and services during the procurement process.
Vendor contract management: Manage vendor contracts and legal aspects of the relationship. Data Processing Agreements are usually annexed to the service agreement, and they dictate the rules to subprocess confidential data.
Performance evaluation: Assess and monitor vendor performance and control effectiveness via audits, site inspections, and vendor questionnaires.
Security scorecards: Assess vendors across a benchmark of risk domains, and assign a grade ranking to signify the vendor risk level.
Frameworks and regulatory standards: Publications issued by policymakers, regulatory bodies, or accredited professional associations to guide organizations on their obligations
Organizations can perform these activities and track them manually using templates and spreadsheets.
While this approach is suitable when there are only a few vendors and minimal operational complexity to account for, the program becomes time-consuming and challenging to manage as volume increases, regulatory requirements intensify, and transactions get complex.
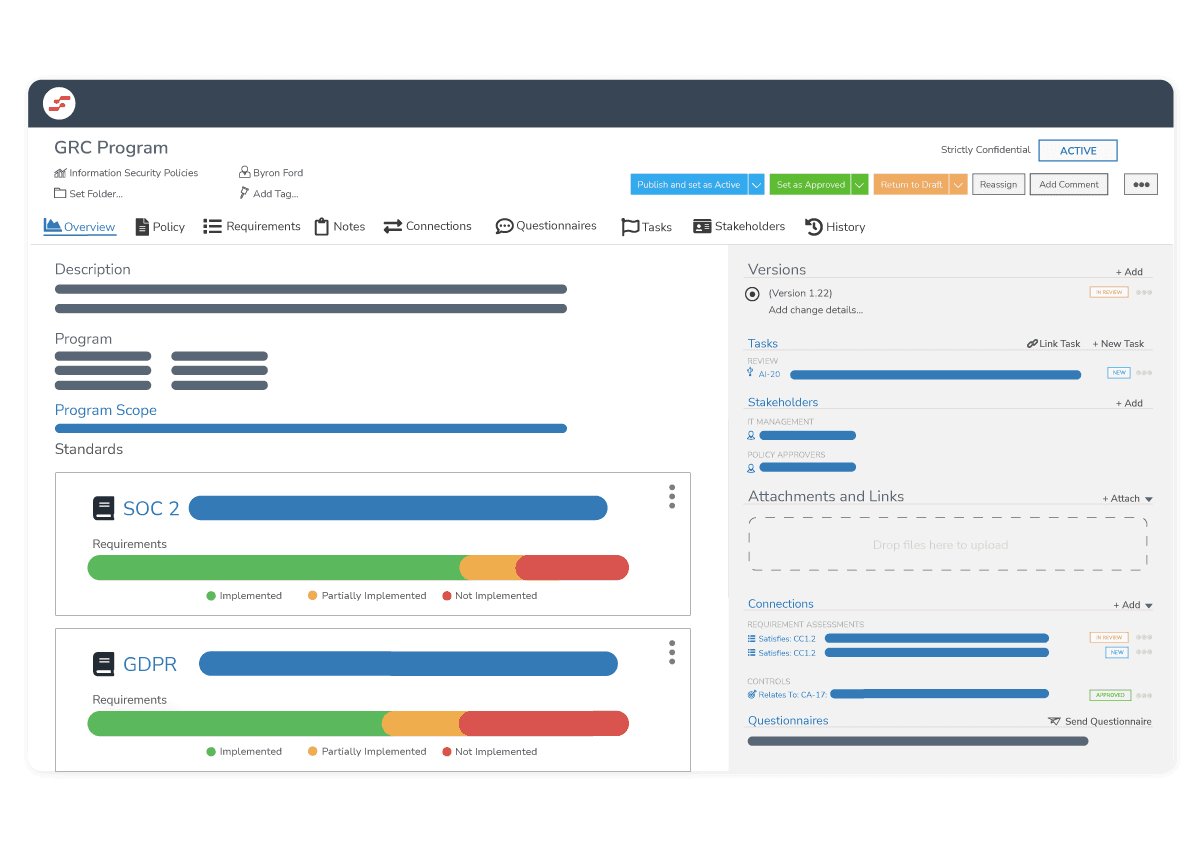
In recent years, technological innovations and the transition to cloud-based services have given rise to modern solutions that can help organizations transform and scale their VRM program via automation, integration, and enhanced data analytics capabilities.
These solutions, whether complete GRC platforms or VRM-specific solutions have revolutionized how we manage vendor risks in the best way possible by bringing everything together.
You can achieve this through a centralized database for vendor contract and performance tracking, consistent methodology for managing risks, simplified and automated vendor assessments, real-time and transparent reporting capabilities, and seamless integration with existing systems.
Key Takeaways
Outsourcing is a popular business strategy that can lead to cost savings and operational efficiency but also introduces risks associated with vendor relationships.
VRM is a critical component of ERM that helps organizations identify and mitigate risks associated with their vendors and third-party service providers.
Vendor Risk Management is also vital because emerging privacy regulations, infosec standards, interconnected systems, and resilience are becoming hot topics.
Implementing an effective VRM program can minimize the harmful impacts of vendor disruptions.
Manual tracking of VRM activities can become time-consuming and challenging to manage as volume increases and transactions get complex.
Technological innovations and cloud-based services have given rise to modern solutions that can help organizations transform and scale their VRM program via automation, integration, and enhanced data analytics capabilities.
Reach out to our team and schedule a demo to assist you with anything you need for your Vendor Risk Management Program. StandardFusion's platform helps you with vendor identification, vendor questionnaires, contact management, vendor assessment, and more.
Here, you can navigate to parts two and three:
The foundations and Benefits





