Published on: Jan 3, 2024
| Updated: Apr 11, 2025
Third-Party Risk Management: Everything You Need to Know To Protect Your Organization
Third-party risk management plays a pivotal role in safeguarding businesses from external threats.
In this in-depth guide, we'll discuss the core aspects of TPRM, highlighting the distinctions between third and fourth parties, the various risks they might bring, and the best practices you should follow.
We'll also talk about the benefits of dedicated TPRM software and its role in strengthening an organization's defence mechanisms.
Let's begin!
What Is a Third Party?
A third party in cybersecurity refers to an external entity or organization that is not directly involved in a particular transaction or system but can still impact its security.
Third parties often provide services, software, or components that organizations rely on to operate efficiently. These external entities can include vendors, suppliers, contractors, or any external party with whom an organization shares data or access to its systems.
What is a Fourth Party?
A fourth party refers to an entity or organization that indirectly interacts with your network or data systems, often through intermediaries or third-party connections. Unlike a third party, which has a direct relationship with your organization, fourth parties are further removed but can still present significant security risks.
How is a fourth party Related to a Third-Party?
The relationship between fourth parties and third parties is hierarchical. Third parties directly engage with your organization, providing services or accessing your data. Fourth parties, on the other hand, are entities that have relationships with your third-party partners.
In essence, they are your third-party's third party. The actions of fourth parties can indirectly impact your cybersecurity posture and approach.
Why is it Important to Know About Fourth Parties?
Understanding fourth-party relationships is crucial for several reasons. Here are some examples to illustrate their significance:
Risk Management: Imagine your organization uses a cloud hosting service (third-party). This service relies on a data centre provider (another third party) to maintain its infrastructure. If the data centre provider experiences a security breach, your cloud hosting service (a fourth party to you) could also be compromised, potentially putting your data at risk.
Compliance: Suppose you're a healthcare provider outsourcing medical billing to a third-party company. That third party, in turn, relies on a software vendor for their billing platform (a fourth party to you). Compliance with healthcare regulations extends not just to your direct relationship with the billing company, but also to their interactions with the software vendor.
Incident Response: Consider a scenario where a major retail chain (third-party) experiences a data breach. This breach may have cascading effects on various suppliers (fourth parties) who also have access to the retail chain's systems. Awareness of these fourth-party connections would be vital in orchestrating a swift incident response to contain and mitigate the breach.
Risk Mitigation: If your organization uses a third-party IT security consultancy, it's essential to inquire about their subcontractors or partners (fourth parties) involved in your security assessments. Understanding their role and cybersecurity measures ensures that your organization's vulnerabilities are not inadvertently exposed through these relationships.
Vendor Assessment: When assessing the cybersecurity practices of a third-party logistics provider, it's imperative to extend your scrutiny to the transportation companies they engage (fourth parties). These transportation partners can have access to your sensitive shipments and data during transit.
Industries such as healthcare, banking, and federal contracting are heavily influenced by regulatory standards that shape Third-Party Risk Management (TPRM) programs. These industries must adhere to comprehensive regulatory frameworks due to the sensitive data they handle, driving the need for robust TPRM processes.
Regulatory Frameworks and Compliance:
For example, the Payment Card Industry Data Security Standard (PCI-DSS) is a critical regulatory framework that impacts TPRM. It mandates that companies not only secure their own cybersecurity programs but also ensure their third-party providers do not compromise cardholder data security. This highlights the intricate web of compliance that extends to fourth parties in your supply chain.
Federal Contracting Requirements:
In federal contracting, strict security measures are compulsory for all vendors with access to sensitive information. The process requires more than just documentation; it involves thorough checks like scanning internal environments and obtaining legal assurances from executives about data protection measures.
The intricate complexities and potential conflicts in these regulated industries drive companies to continuously enhance their risk management and mitigation strategies. By understanding and managing both third and fourth-party relationships, organizations can better navigate the compliance landscape and protect their data integrity.

Now, let's talk about what you came for!
What is Third-Party Risk Management?
Third-Party Risk Management (TPRM) is a vital aspect of corporate governance and cybersecurity. It involves the assessment, monitoring, and mitigation of risks associated with the engagement of external parties, such as vendors, suppliers, contractors, or service providers, who have access to a company's data, systems, or operations.
In today's complex landscape, ongoing geopolitical crises, catastrophic climate events, unexpected supply chain disruptions, and increasing third-party cybersecurity threats have necessitated the rapid implementation of robust TPRM programs. Organizations are leveraging these programs to manage the risks posed by third parties effectively.
In essence, TPRM seeks to ensure that these third parties do not pose a threat to the organization's security, compliance, reputation, or operational continuity. It encompasses various processes, including due diligence, risk assessment, contractual agreements, ongoing monitoring, and response planning.
Key Functions of TPRM:
Managing Cybersecurity Risks: Most TPRM executives focus on managing cybersecurity threats, ensuring that third parties adhere to security protocols to protect sensitive data and systems.
Enabling Data Governance: By implementing TPRM, organizations can streamline their data governance efforts, ensuring that third parties comply with data handling and privacy standards.
Improving Cost Efficiency: TPRM programs are designed to optimize resource allocation, minimizing unnecessary expenditures while maintaining high standards of security and compliance.
Keep in mind the following:
While Third-Party Risk Management and Vendor Risk Management (VRM) are closely related concepts, they are not entirely interchangeable.
Vendor Risk Management (VRM) is a subset of Third-Party Risk Management. VRM specifically focuses on evaluating and managing the risks associated with vendors and suppliers who provide goods and services to an organization. This often includes assessing financial stability, product quality, delivery performance, and compliance with contractual terms.
Third-Party Risk Management (TPRM) takes a broader perspective, encompassing all external parties, including vendors but also extending to contractors, service providers, and any other entities that interact with the organization. TPRM addresses not only the operational and financial aspects but also information security, data privacy, regulatory compliance, and reputational risks.
By integrating these functions, TPRM strengthens an organization's resilience against both anticipated and unexpected threats, ensuring a more secure and efficient operational environment.
Regulatory and Compliance Requirements Driving TPRM
A comprehensive TPRM program is often shaped by various regulatory and compliance requirements. These regulations provide a framework for managing third-party risk effectively. Key regulations and guidelines include:
CMMC, EBA, FCA, FFIEC, HIPAA, NERC, NIST, NYDFS, OCC: These are specific to different sectors and dictate standards for data security and vendor management.
GDPR and CCPA: These focus on data privacy and protection, especially concerning customer data, influencing how organizations manage third-party relationships.
Factors Influencing Regulatory Requirements
Organization Type and Location: Regulations may vary depending on whether your organization is a financial institution, healthcare provider, or another type of entity.
Customer Location: Knowing where your customers reside is crucial as it determines the data protection laws applicable to your operations.
Understanding these requirements ensures your TPRM program accounts for the data your organization must protect and establishes the standards your vendors must meet. These requirements are essential to include in agreements with vendors handling sensitive or regulated data.
To sum up!
While Third-Party Risk Management and Vendor Risk Management share common elements, they serve different purposes within the overall risk management framework of an organization. TPRM covers a wider range of external relationships, making it a more comprehensive approach to mitigating risks associated with third parties.
The Evolution of Third-Party Risk Management (TPRM)
From Annual Checklists to Daily Essentials
Third-Party Risk Management (TPRM) has transformed remarkably over the years. Originally seen as a once-a-year task, it’s now an indispensable part of daily operations for businesses around the globe. This evolution reflects the increasing complexity and interconnectedness among companies, vendors, and global partners.
The Shift from Emails to Automation
Years ago, TPRM activities largely revolved around exchanging emails—an approach that was not only cumbersome but also lacked depth. Fast-forward to today, and TPRM has embraced advanced methodologies. Current practices involve continuous monitoring techniques that leverage automation, enabling businesses to react swiftly to potential threats.
Integration with Technology and Collaboration
Modern TPRM combines traditional due diligence with cutting-edge technology. This means integrating data analytics, real-time insights, and automated alerts, which result in a more proactive risk management strategy. By incorporating these tools, businesses can better anticipate disruptions caused by incidents anywhere in the world.
Adapting to a Globalized Business Environment
In an era where a distant disruption can instantly impact client services, TPRM's role has become more critical than ever. It now entails a comprehensive understanding and real-time management of risks—highlighting just how vital these evolved practices are in maintaining operational resilience and stability.
What are the Primary Drivers for Implementing a TPRM Program?
Implementing a Third-Party Risk Management (TPRM) program is crucial for modern organizations, and several key factors drive this necessity:
1. Regulatory Compliance
Organizations are often required to adhere to a wide range of regulations that dictate how they manage third-party risks. These regulations vary depending on the industry and geographic location and include frameworks like the GDPR, HIPAA, and CCPA. Such regulations compel companies to safeguard both their data and that of their customers, making compliance a significant motivator for establishing a TPRM program.
2. Cybersecurity Concerns
In an era where data breaches and cyberattacks are increasingly common, managing cybersecurity risks is paramount. A robust TPRM program helps mitigate the threat posed by third-party vendors who might otherwise be a weak link in an organization's security chain.
3. Gaining Competitive Edge
An effective TPRM program can serve as a differentiator in the marketplace. Companies that manage their third-party risks efficiently are more likely to gain the trust of clients and stakeholders, providing them with a competitive advantage over those that do not prioritize third-party risk management.
4. Operational Efficiency and Cost Control
Beyond external regulations and market positioning, internal drivers such as improving purchasing efficiency and managing operational risks encourage the adoption of TPRM programs. Streamlining vendor management reduces waste and saves costs, leading to more efficient internal processes.
5. Customer Demands
Finally, many organizations find that meeting customer expectations and demands for data protection and vendor accountability is a critical driver. Customers increasingly expect their data to be handled safely, compelling companies to establish TPRM programs to assure their clients of this capability.
By addressing these key factors, organizations can not only comply with necessary regulations and reduce risk but also enhance their market position and operational efficiency. The integration of these elements into a TPRM program is essential for sustainable success.
What Types of Risk Can Third Parties Introduce?
When organizations collaborate with third-party vendors, they expose themselves to various cybersecurity risks and other associated threats. These risks can broadly be categorized into several key areas, let's check some of them:
1. Cybersecurity Risk
Third-party vendors may not have the same level of security measures in place as the organization, making them potential weak points for cyberattacks. These risks could manifest as data breaches, malware infections, or unauthorized access to sensitive information through vulnerabilities in the vendor's systems or practices.
2. Operational Risk
Working with third parties introduces operational risks, such as disruptions in service delivery or supply chain interruptions. These can result from vendor errors, service outages, or other operational issues that impact the organization's ability to function effectively.
3. Legal/Regulatory Risk
Organizations must ensure that their third-party partners comply with relevant laws and regulations. If a vendor violates data protection or privacy laws, for example, the organization could face legal consequences and reputational damage. Legal and regulatory risks may also arise from contractual disputes or non-compliance with industry-specific standards.
4. Reputation Risk
If a third-party vendor experiences a cybersecurity breach or scandal, the organization associated with them can suffer reputational damage by association. Negative publicity can erode trust among customers, investors, and other stakeholders.
5. Financial Risk
Costs related to cybersecurity incidents, operational disruptions, or legal actions against vendors can have financial implications for the organization. These expenses might include breach response, litigation, fines, and loss of revenue.
6. Supply Chain Risk
Organizations reliant on third-party vendors for critical components or services face supply chain risks. Disruptions in the vendor's supply chain, such as natural disasters, geopolitical events, or financial instability, can disrupt the organization's operations.
7. Vendor Dependency Risk
Over-reliance on a single vendor for a particular service or product can create vendor dependency risk. If that vendor experiences issues or goes out of business, the organization may struggle to find alternatives quickly, impacting its operations.
Now, to mitigate these risks, organizations should conduct thorough due diligence when selecting vendors, establish clear contractual agreements that address security and compliance, monitor vendor performance, and develop contingency plans for potential disruptions.
Regular security assessments, audits, and ongoing communication with third-party vendors are essential to maintaining a robust cybersecurity posture in today's interconnected business landscape.
Key Considerations for Establishing a TPRM Program: Internal and External Stakeholders
Involving Internal Stakeholders
When setting up a Third-Party Risk Management (TPRM) program, comprehensively involving your internal stakeholders is crucial. This ensures alignment across the board, setting the foundation for a robust and effective program. The internal audience typically includes:
Leadership Team: Key decision-makers like the CEO, CFO, CIO, COO, and CISO play an essential role in resource allocation and strategic direction.
Legal and Compliance: General Counsel ensures the program aligns with legal requirements and mitigates potential legal risks.
Board Members: Provide oversight and strategic input that bolster the program's credibility and effectiveness.
Internal Auditors: Offer insights into financial and operational risks, ensuring processes are adhered to.
Depending on the scope and nature of your operations, other internal parties may also be vital. Evaluate based on your organization’s specific needs.
Engaging External Stakeholders
External stakeholders are equally significant in crafting a TPRM program. They not only influence but also help in fine-tuning the program. These include:
Vendors: Critical partners whose compliance and security posture directly affect your own risk management.
Regulators: Their expectations and guidelines must be heeded to meet industry standards and regulatory compliance.
Customers: They demand transparency and assurance, which are reflected in a robust TPRM program.
Assess Existing Agreements
Another key aspect is the evaluation of current agreements and relationships with third parties. Analyze these meticulously against your proposed TPRM program to identify any discrepancies. Be proactive in documenting these gaps and strategizing on mitigating uncovered risks, following up diligently until resolutions are achieved.
In summary, creating a successful TPRM program requires a balanced approach involving both internal and external players, coupled with a keen eye on current contracts. Tailor this framework to suit your organization’s unique ecosystem for optimal results.
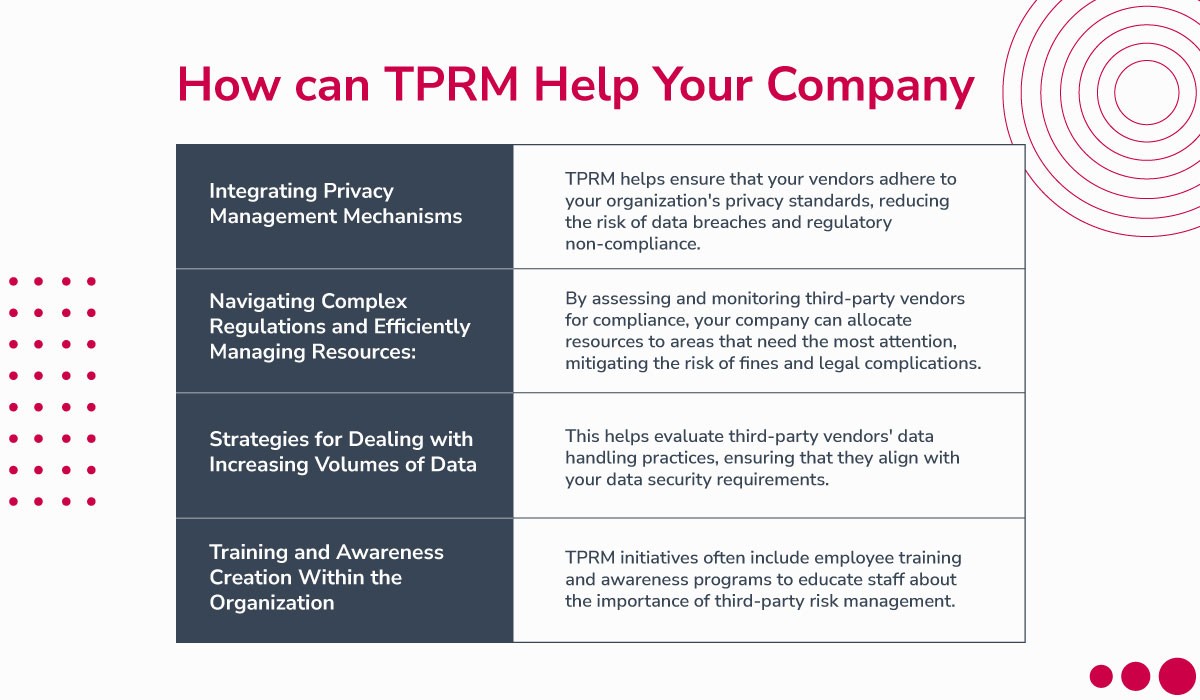
How Can Third-Party Risk Management Help Your Company
Third-Party Risk Management (TPRM) plays a crucial role in enhancing your company's overall security and compliance. Here's a comprehensive and concise overview of how TPRM can benefit your organization in four key areas:
1. Integrating Privacy Management Mechanisms: TPRM assists your company in addressing the challenges of incorporating robust privacy management mechanisms. With the growing importance of data privacy regulations like GDPR and CCPA, third-party vendors often handle sensitive customer data. TPRM helps ensure that these vendors adhere to your organization's privacy standards, reducing the risk of data breaches and regulatory non-compliance.
2. Navigating Complex Regulations and Efficiently Managing Resources: Keeping up with evolving and intricate regulations can be daunting. TPRM provides a structured framework for understanding and complying with these regulations. By assessing and monitoring third-party vendors for compliance, your company can efficiently allocate resources to areas that need the most attention, mitigating the risk of costly fines and legal complications.
3. Strategies for Dealing with Increasing Volumes of Data: As businesses generate and handle vast amounts of data, TPRM offers strategies to manage the associated risks. It helps evaluate third-party vendors' data handling practices, ensuring that they align with your data security requirements. This proactive approach helps protect sensitive information and maintain data integrity as the volume of data continues to grow.
4. Training and Awareness Creation Within the Organization: TPRM extends beyond vendor assessment; it involves creating a culture of security and compliance within your organization. TPRM initiatives often include employee training and awareness programs to educate staff about the importance of third-party risk management. This helps foster a security-conscious workforce that can actively contribute to risk mitigation efforts.
In a nutshell:
Third-Party Risk Management assists your company in integrating privacy management mechanisms, navigating complex regulations, efficiently managing resources, and addressing the challenges posed by increasing volumes of data. Additionally, it fosters a culture of awareness and preparedness within your organization to mitigate third-party-related risks effectively.
How Can You Assess a Vendor?
Assessing a vendor through third-party risk assessment involves several crucial methods to ensure the security and reliability of external partnerships. First, it is essential to conduct thorough due diligence by gathering information on the vendor's financial stability, reputation, and compliance with relevant regulations.
Secondly, evaluate the vendor's cybersecurity measures and data protection practices to gauge their ability to safeguard sensitive information. Additionally, consider the vendor's historical performance and track record with other clients to assess their reliability.
Collaborating with third-party assessment firms and leveraging industry-specific benchmarks can provide valuable insights. Regular monitoring and ongoing communication with the vendor are also key elements in the assessment process to ensure continued compliance and risk mitigation.
How Can You Address Gaps In Your Vendor Risk Management Process?
To effectively address gaps in their vendor risk management processes, organizations should focus on a few critical steps. Firstly, they need to perform a comprehensive assessment to clearly identify where vulnerabilities exist. This involves evaluating current practices and contrasting them against industry standards and benchmarks to understand where improvements are necessary.
Once the gaps are identified, it's crucial to implement robust processes and protocols that directly address these weaknesses. This may include enhancing due diligence practices, improving contract terms, or employing advanced monitoring tools to track vendor behavior and performance consistently.
Additionally, organizations should invest in training and awareness programs that equip their teams with the necessary skills to manage and mitigate third-party risks effectively. Regular training sessions can keep everyone updated on new strategies and regulatory requirements, ensuring the whole team is proficient in managing vendor relationships.
Finally, leveraging technology plays a significant role in bolstering vendor risk management. Utilizing tools like risk management software can streamline the assessment process, automate routine checks, and provide real-time data analytics for informed decision-making. By taking these steps, businesses can not only patch existing vulnerabilities but also fortify their operations for sustained growth and confidence in their partnerships.
What Questions Should Organizations Ask When Implementing a TPRM Program?
When an organization is ready to implement a Third-Party Risk Management (TPRM) program, it needs to ask crucial questions to ensure success. Here are key considerations:
Determine Your Support Structure
External Assistance: Should you collaborate with a third-party expert to kickstart and manage the program effectively?
Define Roles and Responsibilities
Internal Expectations: How will you communicate and manage expectations with internal stakeholders, ensuring everyone is aligned?
Responsibility Designation: What specific roles and responsibilities need to be assigned, particularly in the event of a data breach or other risks?
Establish Third-Party Criteria
Requirement Standards: What specific criteria must third parties meet to align with your business standards?
Communication Clarity: Do external partners fully understand these requirements, and are they equipped to implement them?
Evaluate Financial Implications
Financial Impact: Could these new requirements alter the financial dynamics with your vendors and thus require renegotiations?
Integrate with Existing Relationships
Program Rollout: What strategies will you employ to incorporate this program into your current vendor relationships without disruption?
Addressing these questions carefully can pave the way for a comprehensive and effective TPRM program that safeguards your organization while maintaining healthy third-party relationships.
What is the Lifecycle of a TPRM Program and What are its Key Phases?
A Third-Party Risk Management (TPRM) program is essential for organizations to manage and mitigate risks associated with external vendors. Understanding its lifecycle provides a roadmap for effective management across various stages. Here’s a detailed look at the key phases:
1. Sourcing and Selection
The initial phase focuses on selecting the right vendors by assessing their capabilities and potential risks. This involves:
Evaluating their ability to meet service requirements.
Analyzing baseline risks such as security, privacy, and financial stability.
Using tools like questionnaires or third-party intelligence databases for assessments.
2. Intake and Onboarding
Once suitable vendors are chosen, a seamless onboarding process is crucial. This includes:
Integrating vendor information into a central system either manually or through bulk uploads.
Utilizing intake forms, spreadsheet imports, or APIs linked to existing vendor management systems.
3. Inherent Risk Scoring
Before allowing vendors access to critical systems, you must:
Determine the inherent risk, which is the risk present before any mitigating controls.
Conduct preliminary risk assessments to guide the level of due diligence and set the framework for ongoing evaluations.
4. Internal Controls Assessment
This stage involves scrutinizing the vendor's internal processes, with a focus on:
Performing due diligence through controls assessments.
Scoring risks based on factors like impact and likelihood.
Mapping assessment results to compliance frameworks, such as ISO, NIST, or SOC 2.
5. External Risk Monitoring
Keep tabs on vendors beyond periodic assessments by:
Leveraging external sources for continuous intelligence.
Incorporating elements like cyber intelligence, financial reports, and breach alerts.
Covering gaps and validating vendor-provided information with real-time data.
6. SLA and Performance Management
Evaluate the ongoing performance of vendors by:
Ensuring they meet Service Level Agreements (SLAs) and compliance obligations.
Monitoring their ability to address issues and apply necessary remediations.
7. Offboarding and Termination
The final phase ensures a smooth end to the business relationship:
Reviewing contracts, settling accounts, and revoking access to systems and data.
Ensuring privacy and security compliance is maintained throughout the exit process.
Navigating the TPRM lifecycle effectively helps safeguard your organization from potential third-party risks, ensuring compliance and smooth vendor management throughout the entire relationship.
TPRM Best Practices
Third-party risk management (TPRM) is a crucial aspect of modern business operations, as organizations increasingly rely on external vendors, suppliers, and partners to meet their operational needs.
To establish an effective TPRM strategy, it's essential to follow best practices that help mitigate risks and ensure smooth operations.
Here are some key TPRM best practices:
1. Risk Assessment and Prioritization
Begin by identifying and categorizing third-party relationships based on their criticality and potential impact on your organization. Not all vendors pose the same level of risk, so prioritize accordingly. Analyze the vendor risk profile alongside the risk profile of the engagement or the service provided. This targeted analysis helps in tailoring risk management efforts more effectively.
2. Due Diligence
Conduct thorough due diligence before onboarding any third party. This includes evaluating their financial stability, reputation, security practices, and compliance with regulatory requirements. Set organizational standards and language to ensure consistency in evaluations and expectations.
3. Contractual Agreements
Clearly define expectations and responsibilities in contracts and service level agreements (SLAs). Specify security and compliance requirements, data protection measures, and dispute resolution mechanisms. Include minimum performance standards and consider 'rewards' for compliance with critical risk management functions.
4. Continuous Monitoring
Regularly monitor and assess third-party performance and risk throughout the relationship. Implement automated tools and processes for real-time tracking of compliance and security issues. Enable a reporting process driven by dynamic monitoring and risk assessment based on events.
5. Vendor Security Assessments
Conduct security assessments to evaluate a vendor's cybersecurity posture. Assess vulnerabilities, data protection practices, and incident response capabilities. Integrate technology solutions to unify procurement, performance, and risk management, providing stakeholders with updated information on demand.
6. Regulatory Compliance
Stay up-to-date with relevant industry regulations and ensure that third parties also comply with these regulations. Regularly review and update contracts to reflect any changes in regulatory requirements.
7. Data Protection and Privacy
Protect sensitive data by ensuring that third parties follow robust data protection and privacy practices. Establish protocols for data sharing, encryption, and secure data disposal.
8. Business Continuity Planning
Assess third-party vendors' business continuity plans to ensure they can maintain operations during disruptions or disasters. Consider redundancy and backup options.
9. Incident Response Planning
Develop incident response plans that include third-party involvement. Clarify roles and responsibilities for handling security incidents and breaches.
10. Communication and Training
Foster a culture of awareness and responsibility within your organization. Provide training to employees regarding TPRM policies and procedures, emphasizing the importance of vigilance.
11. Escalation Protocols
Establish clear escalation paths for addressing issues with third parties. Define who to contact and what steps to take in case of non-compliance or major risks.
12. Documentation and Reporting
Maintain comprehensive records of all TPRM activities, assessments, and communications. Regularly report to senior management and stakeholders on the status of third-party relationships and associated risks.
13. Flexibility and Adaptation
Be prepared to adapt your TPRM strategy as risks evolve and your organization's needs change. Continuous improvement is key to effective risk management. By leveraging areas of existing compliance, it is possible to lower costs for both parties to their mutual benefit.
Incorporating these TPRM best practices into your organization's strategy will help minimize risks associated with third-party relationships and promote operational resilience. It's essential to view TPRM as an ongoing process that evolves to meet the dynamic challenges of the business landscape.
Why You Should Invest in Third-Party Risk Management
Investing in Third-Party Risk Management (TPRM) is a strategic decision that offers numerous benefits to organizations in various industries. Here are some compelling reasons why you should consider investing in TPRM:
1. Cost Reduction: TPRM can lead to significant cost savings by helping organizations identify and mitigate risks associated with their third-party vendors. Proactively addressing potential issues, like data breaches or operational disruptions, organizations can avoid costly incidents and legal liabilities.
2. Security: TPRM enhances cybersecurity by ensuring that third-party vendors meet security standards and adhere to data protection regulations. This safeguards sensitive information and reduces the risk of data breaches, which can be devastating for both a company's reputation and its bottom line.
3. Compliance: Regulatory compliance is a critical aspect of modern business operations. TPRM assists organizations in ensuring that their third-party vendors comply with industry-specific regulations and standards. This not only helps avoid fines and penalties but also fosters trust among stakeholders.
4. Risk Reduction: TPRM enables organizations to proactively identify and mitigate risks associated with third-party relationships. Comprehensive risk assessments and ongoing vendor performance monitoring minimize the chances of disruptions and financial setbacks.
5. Confidence: Implementing TPRM instills confidence in stakeholders, including customers, investors, and partners. Knowing that a company has robust third-party risk management practices in place can enhance trust and credibility in the market.
6. Peace of Mind: TPRM provides peace of mind to senior management and boards of directors by offering visibility into the risks posed by third-party relationships. This transparency allows for informed decision-making and ensures that potential risks are managed effectively.
To wrap things up:
Investing in Third-Party Risk Management is imperative for organizations looking to protect their reputation, reduce costs, enhance security, ensure compliance, and build confidence among stakeholders. It is a proactive approach that not only mitigates risks but also contributes to long-term business resilience and success.
What are the Benefits of Third-Party Risk Management Software?
Third-party risk management (TPRM) software offers numerous valuable benefits for organizations. Here are some of the most important advantages of implementing a robust TPRM system:
1. Enhanced Security: TPRM software helps in identifying and mitigating potential security risks associated with third-party vendors. This boosts data security and reduces the chances of data breaches or cyberattacks.
2. Compliance Management: TPRM software ensures third-party vendors comply with industry regulations and internal policies. This helps organizations avoid costly regulatory fines and reputational damage.
3. Risk Reduction: By continuously monitoring third-party relationships, TPRM software helps in identifying and addressing risks in real time. This proactive approach minimizes the impact of potential disruptions on the business.
4. Cost Savings: Effective TPRM software can optimize vendor management processes, reducing administrative overhead and operational costs associated with managing third-party relationships.
5. Vendor Performance: Organizations can assess the performance of their third-party vendors more accurately using TPRM software, enabling them to make informed decisions about vendor retention or termination.
6. Improved Decision-Making: TPRM software provides valuable insights through data analytics, enabling organizations to make data-driven decisions when selecting, onboarding, or renewing third-party contracts.
7. Business Continuity: TPRM software helps in creating contingency plans for third-party disruptions, ensuring business continuity even in the face of unexpected events.
8. Reputation Management: By preventing third-party-related incidents and data breaches, TPRM software safeguards an organization's reputation and builds trust with customers and stakeholders.
9. Streamlined Workflow: Automation features within TPRM software simplify and streamline the vendor assessment and monitoring process, saving time and reducing manual errors.
10. Scalability: As organizations grow and their vendor networks expand, TPRM software can easily scale to accommodate the increasing complexity of managing third-party relationships.
Long story short:
TPRM software plays a crucial role in protecting an organization's interests by identifying, managing, and mitigating risks associated with third-party vendors. It provides a comprehensive solution that enhances security, compliance, decision-making, and cost-efficiency, ultimately contributing to the overall resilience and success of the organization.
What Features Should You Look For in a TPRM Platform?
When considering a Third-Party Risk Management (TPRM) platform, it's essential to prioritize features that align with your organization's specific needs. In this section, we will outline the key features that a robust TPRM platform should encompass.
1. Vendor Assessment and Scoring
A TPRM platform should enable organizations to thoroughly assess vendors comprehensively, assigning risk scores based on various factors such as compliance, security, and performance.
2. Documentation and Data Management
Effective TPRM requires robust document management capabilities, including document storage, version control, and secure access controls.
3. Risk Identification and Monitoring
The platform should facilitate the identification of potential risks associated with third-party relationships and provide continuous monitoring to detect any emerging issues.
4. Compliance Tracking
It's vital that the platform supports regulatory compliance tracking, including auditing capabilities and the ability to align with industry standards and regulations.
5. Incident Management
The TPRM software must assist in incident reporting, tracking, and resolution, helping organizations respond to security breaches or other adverse events promptly.
6. Contract Management
It offers contract lifecycle management features, including automated contract tracking, renewal notifications, and compliance checks.
7. Integration Capabilities
The platform integrates seamlessly with other enterprise systems, such as ERP or CRM, to streamline data sharing and reporting.
8. Alerts and Notifications
Implements alerts and notifications for critical events, helping organizations stay informed about potential risks or compliance issues.
9. Reporting and Analytics
Robust reporting and analytics tools are essential for data-driven decision-making and providing insights into third-party risk posture.
10. User Access Controls
Ensures the platform offers role-based access control to restrict sensitive information access to authorized personnel only.
11. Scalability
A TPRM platform should be scalable to accommodate the growing number of vendors and evolving risk profiles.
12. User-Friendly Interface
An intuitive and user-friendly interface is crucial for the effective utilization of the platform across the organization.
13. Vendor Collaboration
Features for collaborating with vendors, sharing information, sending questionnaires and managing joint mitigation efforts can enhance the effectiveness of TPRM.
14. Automation
Automation of repetitive tasks, such as risk assessments and reporting, can significantly improve efficiency.
15. Training and Support
Access to comprehensive training materials and responsive customer support is vital for effective platform adoption.
Highlighting these features, StandardFusion's TPRM platform offers a comprehensive solution that addresses these critical aspects of third-party risk management. When selecting a TPRM platform, organizations should evaluate how well these features align with their unique requirements and objectives to ensure effective risk management and compliance.
Key Takeaways
Third-party risk management is vital for businesses to protect against external threats in our interconnected world.
While third parties directly interact with an organization, fourth parties are a step removed but can still pose significant security risks.
Risks introduced by third parties can range from cybersecurity threats and operational disruptions to reputational damage and legal complications.
A dedicated software can enhance security, ensure compliance, and streamline vendor assessment processes, among other benefits.
Some of the TPRM best practices are: Emphasizing the need for risk assessment, due diligence, and continuous monitoring. All these will help you effectively manage and mitigate third-party risks.
Some key benefits of Third-party Risk Management:
Cost Savings: Avoid financial pitfalls through proactive management.
Enhanced Security: Reduce potential data breaches by ensuring third-party security standards.
Compliance: Ensure alignment with industry regulations.
Operational Stability: Address risks early for smoother business operations
TPRM is more than just vendor risk management. Third-party risk management covers a wide range of external relationships, offering a comprehensive approach to risk management.
In today’s complex business landscape, managing third-party risks effectively is mandatory.
With StandardFusion’s GRC software, you will get a tailored solution that not only addresses your unique challenges but also fits seamlessly with your operations.
If you are seeking a scalable, user-friendly, and comprehensive tool, connect with our team to get more information on how to get started.






