Published on: Jun 22, 2024
| Updated: Apr 11, 2025
NIST SP 800-53 Rev. 5 and FedRAMP: A Comprehensive Guide
Learn exactly what you need to know about the NIST SP 800-53 Rev. 5 (latest update) and how it relates to FedRAMP.
This article will show you how these frameworks shape the security landscape for Federal Information Systems and Cloud Service Providers.
Let's dive right into it!
What is NIST SP 800-53?
NIST Special Publication 800-53 is a special security and privacy standard that created sets of controls for Federal Information Systems and Organizations.
The NIST is a non-regulatory agency of the U.S. Commerce Department and was established to encourage and assist innovation and science by promoting and maintaining a set of industry standards.
Let's dig a little deeper.
NIST SP 800-53 is a set of standards and guidelines to help federal agencies and contractors meet the requirements set by the Federal Information Security Management Act (FISMA).
NIST SP 800-53 Rev. 5
NIST SP 800-53 Rev. 5 introduces significant enhancements in various areas:
Privacy Controls: New and updated controls to better protect personal information, addressing the need for robust privacy governance and accountability.
Supply Chain Risk Management: Guidelines to ensure information technology products are sufficiently trustworthy, incorporating the latest threat intelligence to mitigate risks.
Control Families: Improved and expanded control families to address specific areas of concern, such as cyber resiliency and secure systems design.
System and Information Integrity: Enhanced controls to maintain the integrity of information systems, supported by data on recent cyber-attack trends.
Physical and Environmental Protection: Updated controls to protect physical and environmental aspects of information systems, ensuring comprehensive security measures.
Incorporating these new, state-of-the-practice controls strengthens both security and privacy frameworks. These enhancements are informed by the latest threat intelligence and cyber-attack data, making them critical for organizations aiming to stay ahead in an ever-evolving digital landscape.
Safeguarding Measures in NIST 800-53
The safeguarding measures outlined in NIST Special Publication 800-53 apply to a wide array of computing platforms. These include general-purpose computing systems and extend to more specialized environments.
Key areas covered are:
Cyber-Physical Systems: Integrating both digital and physical components.
Cloud-Based Systems: Encompassing data and services hosted online.
Mobile Devices: Such as smartphones and tablets.
Internet of Things (IoT) Devices: Including smart home gadgets and connected appliances.
Furthermore, these measures are relevant for:
Weapons Systems: Highly specialized defense tools.
Space Systems: Technologies used in outer space exploration.
Communications Systems: Encompassing digital and telecommunication networks.
Environmental Control Systems: Systems managing heating, ventilation, and air conditioning.
Lastly, traditional yet powerful systems like supercomputers, along with industrial control systems that automate manufacturing processes, are also covered. Each platform type is addressed to ensure comprehensive protection across diverse technological landscapes.
How Are the Controls in Revision 5 Made More Outcome-Based?
To make the controls in Revision 5 more outcome-focused, a key change involved reframing them to concentrate on the desired results rather than the entities tasked with implementing them. Here are the elements that contribute to this outcome-based approach:
Focus on Desired Results: Controls have been rephrased to highlight the target outcomes. This shifts attention from the processes and entities involved to the actual security and effectiveness goals they aim to achieve.
Elimination of Specific Assignments: By removing specific mentions of who or what (such as organizations or information systems) is responsible for compliance, the controls encourage a broader and more flexible application. This allows for diverse methods and strategies to be employed, as long as they meet the intended goals.
Emphasis on Flexibility and Innovation: Encouraging entities to determine their unique ways of achieving the set objectives fosters innovation and allows for more tailored security solutions. This adaptability is essential in varying environments or rapidly evolving tech landscapes.
Universal Applicability: The redesign cultivates an environment where controls can be applied universally across different systems and structures, ensuring they remain relevant and effective regardless of the specific landscape.
Ultimately, shifting towards outcome-based controls enhances clarity and sets a clear standard for what needs to be achieved, rather than prescribing how it should be done.
FedRAMP Program
FedRAMP is a U.S. government program that standardizes the security assessment, authorization, and continuous monitoring of cloud products and services. Its primary goal is to speed up the adoption of secure cloud solutions across the federal government.
This government program uses NIST 800-53 Rev. 5 controls as the baseline for its security requirements.
In short, this means that cloud service providers seeking FedRAMP authorization must demonstrate compliance with the security controls outlined.
FedRAMP categorizes cloud services into three impact levels: Low, Moderate, and High.
Each level corresponds to the sensitivity of the data handled and has its own set of security controls derived from NIST SP 800-53.
This categorization ensures that security measures are tailored to the specific risk profiles of different systems, enabling a more targeted and effective approach to cybersecurity.
Now, let's talk about the controls and their relationship with FedRAMP.
NIST SP 800-53 Rev. 5 Controls and FedRAMP
As we mentioned, NIST 800-53 Rev. 5 includes a set of security controls organized into families.
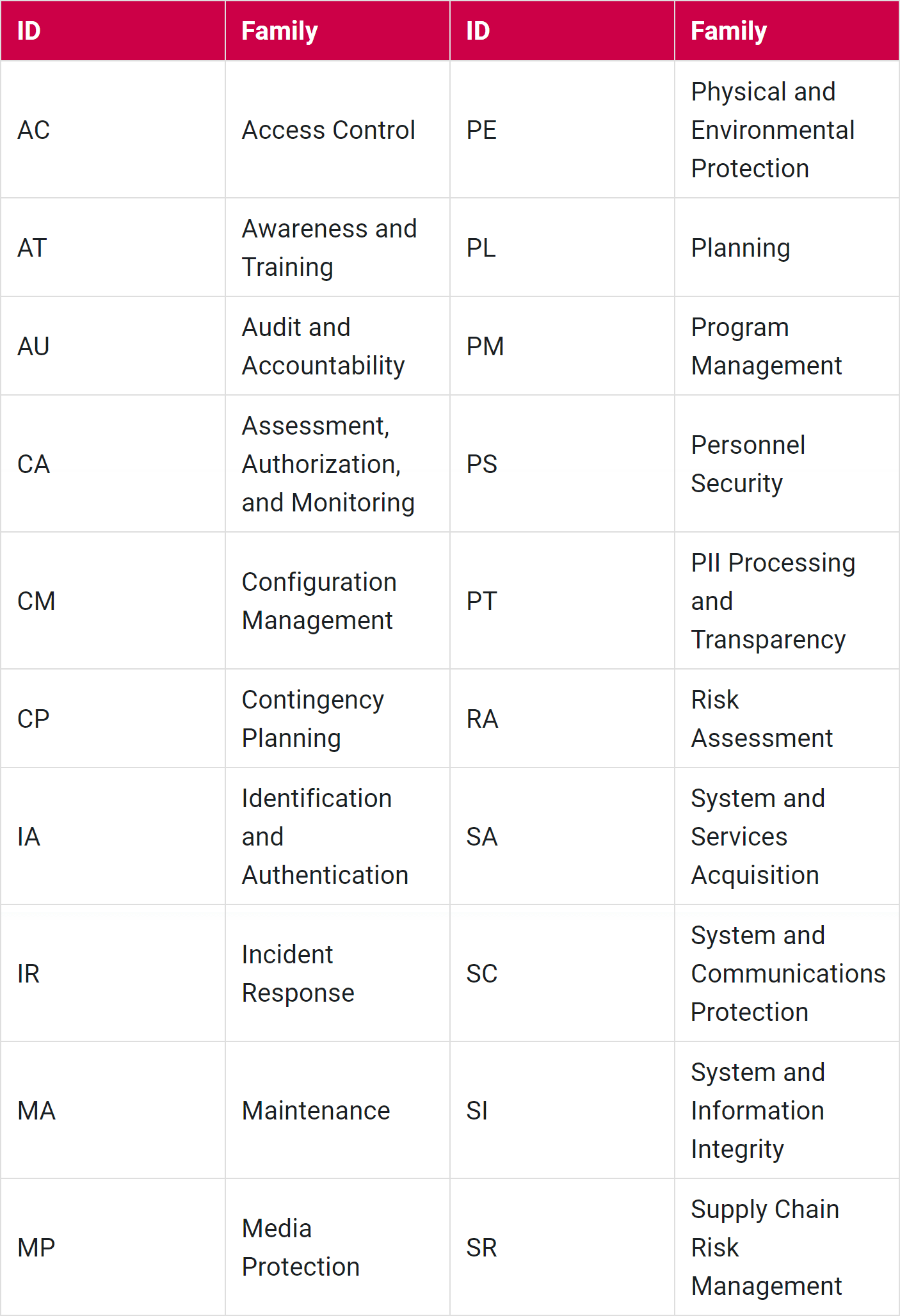
Here is a brief overview of NIST 800-53 Rev. 5's 20 control families:
Access Control (AC): Restrict and manage access to information systems and data.
Awareness and Training (AT): Promote security awareness and provide training programs to enhance the knowledge and capabilities of personnel, reducing security risks associated with human factors.
Audit and Accountability (AU): Ensure accountability, detect incidents, and support investigations.
Assessment, Authorization, and Monitoring (CA): Assess and authorize information systems for use and continuously monitor to ensure ongoing compliance and security.
Configuration Management (CM): Establish and maintain a secure baseline configuration for information systems.
Contingency Planning (CP): CP is designed to establish effective measures for preparing and responding to disruptions in information system operations. The goal is to ensure the availability and integrity of critical systems and data during and after incidents.
Identification and Authentication (IA): The Identification and Authentication control family aims to establish and enforce processes that uniquely identify and verify the identity of users, devices, and processes accessing information systems. This is crucial for ensuring that only authorized entities gain access to system resources.
Incident Response (IR): Prepare for, detect, respond to, and recover from security incidents.
Maintenance (MA): System maintenance addresses the information security aspects of the system maintenance program and applies to all types of maintenance to system components conducted by cloud providers.
Media Protection (MP): This control family focuses on safeguarding physical and digital media containing information. The objective is to prevent unauthorized access, disclosure, alteration, and destruction of sensitive information stored on various types of media.
Physical and Environmental Protection (PE): This control family includes controls and guidelines to address the security of physical spaces, equipment, and environmental conditions. Moreover, this encompasses measures to safeguard information systems against physical threats, environmental hazards, and unauthorized access.
Planning (PL): Planning control family refers to a set of controls that focus on establishing and maintaining an organization-wide risk management framework and processes. Furthermore, the objective of the Planning control family is to provide a structured approach to managing risk, ensuring that organizations can identify, assess, and mitigate potential risks to their information systems effectively.
Program Management (PM): This control family defines a set of requirements that focus on establishing and maintaining an organization-wide information security program. The objective is to ensure that an organization has a structured and comprehensive approach to managing information security, encompassing policies, procedures, and governance mechanisms.
Personnel Security (PS): It focuses on establishing and maintaining processes to manage the security of individuals who have access to information systems and data. At last, the objective of the Personnel Security control family is to ensure that individuals with access to sensitive information are trustworthy, reliable, and have the appropriate level of integrity to safeguard the organization's assets.
PII Processing and Transparency (PT): Personally identifiable information processing and transparency policies and procedures address the controls in the PT family that are implemented within systems and organizations. The risk management strategy is an important factor in establishing such policies and procedures. Policies and procedures contribute to security and privacy assurance.
Risk Assessment (RA): Identify, assess, and manage risks to organizational operations and assets.
Systems and Service Acquisition (SA): Its objectives are establishing security controls and measures during the acquisition, development, and implementation of information systems and services. The goal is to ensure that security considerations are integrated throughout the entire life cycle of systems and services, from the initial planning and acquisition stages to deployment and ongoing operations.
System and Communications Protection (SC): Protect the integrity, confidentiality, and availability of information during system and data communication processes.
System and Information Integrity (SI): It focuses on protecting information systems and the integrity of the information processed, stored, and transmitted by those systems. Moreover, the controls in this family aim to ensure that systems operate securely, detect and respond to unauthorized changes, and maintain the integrity of information throughout its lifecycle.
Supply Chain Risk Management (SR): Manage and mitigate risks associated with the supply chain by addressing the need to manage and mitigate risks associated with the supply chain, which includes processes, people, technology, and other resources involved in the development, delivery, and maintenance of information systems.
FedRAMP controls could include:
Applicable at All Levels: Some controls in NIST SP 800-53 Rev. 5 are relevant for all impact levels. For example, AC-14 (Permitted Actions without Identification or Authentication) might apply across all levels, but it's essential to review the latest revision for any changes in control applicability or enhancements.
For Specific Impact Levels: Certain controls are designed only for Moderate and High-impact levels. For instance, AC-12 (Session Termination) may primarily apply to these levels, but verification with the latest Rev. 5 document is recommended to confirm its current categorization.
With Level-Specific Enhancements: Controls like AC-17 (Remote Access) often come with additional enhancements that vary depending on the impact level. In NIST SP 800-53 Rev. 5, there could be new enhancements or alterations in existing ones, tailoring the control more effectively to different security requirements.
Understanding the Impact of Moving Control Baselines and Tailoring Guidance
The decision to transfer control baselines and tailoring guidance from one publication to another, such as NIST SP 800-53B, holds significant importance for several reasons.
Improved Clarity and Organization: By allocating control baselines separately, the content becomes more organized, making it easier for users to distinguish between different sections. This separation can make compliance and implementation guidelines more accessible and user-friendly.
Enhanced Focus on Relationships: It clarifies how requirements relate to controls while emphasizing the link between security and privacy measures. This clarity aids in improving understanding across all levels of an organization, ensuring roles and responsibilities are clear.
Incorporation of Modern Controls: The adaptation involves the integration of advanced controls that keep pace with the latest technological threats and cyber-attacks. By utilizing up-to-date threat intelligence, organizations can bolster their defenses against current threats, ensuring their systems are resilient and secure by design.
Governance and Accountability: Strengthening security and privacy frameworks promotes better governance and accountability. Organizations are better equipped to demonstrate compliance with regulations and standards, fostering trust with stakeholders.
Support for Cyber Resiliency: The enhanced guidance supports the creation of robust systems designed to withstand and recover from cyber threats. This capability is essential for maintaining operational continuity in the face of evolving cyber challenges.
Overall, this strategic move aims to make security frameworks more effective, adaptive, and aligned with contemporary best practices in cybersecurity and privacy.
Selecting Controls
Revision 5 has made significant strides in clarifying the relationship between requirements and controls, as well as the interplay between security and privacy controls. This update is pivotal in helping organizations understand how these elements interact and complement each other.
The choice and execution of security and privacy controls must align with the goals of information security and privacy programs. These objectives and associated risks may operate independently or intersect depending on the context.
Federal information security programs aim to safeguard information and information systems. They ensure confidentiality, integrity, and availability by preventing unauthorized access, use, disclosure, disruption, modification, or destruction.
Additionally, they manage security risks and ensure compliance with relevant security requirements. Federal privacy programs focus on mitigating risks to individuals related to the processing of Personally Identifiable Information (PII). They ensure compliance with applicable privacy requirements.
When a system handles PII, both information security and privacy programs share the responsibility for addressing security risks associated with the PII. The controls chosen to manage these security risks are generally consistent, irrespective of their classification as security or privacy controls in control baselines or program/system plans.
By detaching the selection procedure from the controls, each group can customize their approach to evaluating and implementing necessary measures. This strategy supports a tailored security framework that caters to the requirements of enterprise architects, systems security and privacy engineers, and mission or business owners.
Key Benefits:
Customization: Tailor control use according to the specific requirements of different fields.
Flexibility: Easily adapt and apply controls without being tied to a rigid selection method.
Collaboration: Facilitate cross-disciplinary communication by allowing diverse communities to apply controls that align with their objectives.
This harmonization of security and privacy objectives, as clarified in Revision 5, underscores the importance of a unified approach in managing controls. By clearly defining these relationships, organizations can implement more effective and integrated strategies to safeguard both information and privacy.
Enhancing Understanding and Implementation of Security Controls
In NIST SP 800-53 Rev. 5, each control offers a Discussion section. This section provides detailed information about specific security controls. This guidance helps organizations define, develop, and implement controls tailored to their unique operational contexts.
The Discussion section offers a detailed view of each control, explaining its purpose and application. This is useful when a control needs to be adapted to fit specific business requirements or address particular aspects of an organization's risk assessment.
By reviewing these details, organizations can ensure that their implementation of controls is both effective and relevant to their specific security needs. This section clarifies the control's function and offers insights into its broader implications within an organizational framework.
For controls with broader applications or those that need to be fine-tuned for specific scenarios, the supplemental guidance is helpful. It provides a comprehensive understanding of how a control operates, crucial for both implementing the control effectively and ensuring it aligns with the organization's overall security posture.
Control Enhancements
The section on control enhancements describes security and privacy capabilities that enhance a foundational control. These enhancements are assigned sequential numbers within each control for easy identification when chosen to complement the base control.
Each enhancement has a brief subtitle indicating its intended function or capability. Control enhancements are used with their corresponding base controls. If a control enhancement is chosen, the associated base control must also be selected and implemented.
The references section provides applicable laws, policies, standards, guidelines, websites, and other valuable references pertinent to a specific control or its enhancement. This section includes hyperlinks to publications for additional information on control development, implementation, assessment, and monitoring.
Understanding FedRAMP: Streamlining Cloud Compliance for Federal Agencies
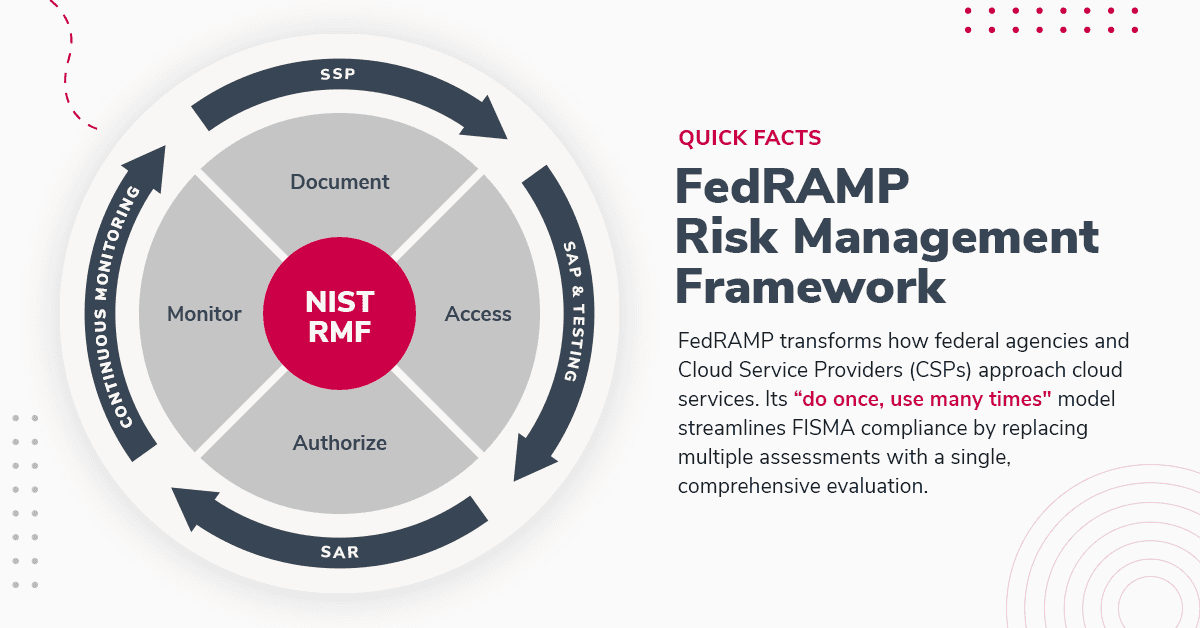
The Federal Risk and Authorization Management Program (FedRAMP) reshapes how federal agencies and Cloud Service Providers (CSPs) approach cloud computing services.
Essentially, it adapts the principles of the Federal Information Security Management Act (FISMA) for the cloud environment, standardizing security in this important area.
FedRAMP operates on a "do once, use many times" framework. This approach is designed to simplify and standardize the process of achieving FISMA compliance for Cloud Service Providers (CSPs).
Instead of multiple individual assessments, CSPs complete a single, comprehensive assessment applicable across various federal agencies.
This streamlines the process and reduces redundancy and costs.
Benefits and Goals
FedRAMP's standardized approach to security and risk assessment for cloud technologies and federal agencies offers key advantages:
Streamline Processes: Minimize inconsistencies and enhance cost-effectiveness by eliminating redundant efforts.
Public-Private Partnership: Foster innovation and advance secure information technologies through collaboration.
Rapid Adoption: Facilitate quick cloud computing adoption within the federal government with transparent standards.
Secure Cloud Utilization: Expand the use of secure cloud technologies across government agencies.
Improved Framework: Enhance the framework for securing and authorizing cloud technologies.
Strong Partnerships: Cultivate and strengthen partnerships with FedRAMP stakeholders.
FedRAMP Authorization Process
You can achieve FedRAMP Authorization through two pathways: securing a provisional authorization via the Joint Authorization Board (JAB) or obtaining authorization through a specific agency.
Agency Authorization Route
In the Agency Authorization route, agencies can collaborate directly with a Cloud Service Provider (CSP) for authorization. When a CSP engages with an agency to pursue an Authority to Operate (ATO), they navigate the FedRAMP Authorization process together.
The process is broken down into three phases:
1. Preparation
Readiness Assessment: CSPs can pursue the FedRAMP Ready designation, recommended for the Agency Authorization process. They work with an accredited Third Party Assessment Organization (3PAO) to conduct a Readiness Assessment. The resulting Readiness Assessment Report (RAR) outlines the CSP's ability to meet federal security requirements.
Pre-Authorization: At this stage, the CSP should have a fully operational system and committed leadership aligned with the FedRAMP process. The CSP engages with FedRAMP by submitting a CSP Information Form and determining the data's security categorization using the FedRAMP Federal Information Processing Standards (FIPS) 199 Categorization Template.
Pre-Authorization Steps:
Ensure a fully built and functional system.
Confirm leadership commitment for FedRAMP compliance.
Engage with FedRAMP through the intake process.
Determine data security categorization using relevant templates and guidelines.
2. Authorization
During the Full Security Assessment step, the 3PAO performs an independent audit of the system. Before this step, the CSP ensures that the System Security Plan (SSP) is complete and reviewed by the agency.
3. Continuous Monitoring
In this phase, the CSP must provide regular security reports (such as vulnerability scans, updated Plans of Action and Milestones, annual security assessments, incident reports, and significant change requests) to all agency customers.
More comprehensive information is available in the Continuous Monitoring Strategy Guide [PDF - 1.1MB].
Every agency using the service assesses the continuous monitoring reports monthly and annually. CSPs use the FedRAMP secure repository to publish monthly monitoring materials, ensuring convenient access and sharing with agency representatives.
Streamlining Compliance Management with StandardFusion
Navigating FedRAMP and NIST SP 800-53 Rev. 5 is not just about adhering to regulations. It's about building trust.
StandardFusion makes this journey straightforward and transparent.
What can help you?
Clear Compliance Path: With StandardFusion, CSPs demonstrate a commitment to security, showcasing adherence to the highest standards.
Reliable Monitoring: Continuous monitoring tools provide real-time insights, reinforcing the reliability of services.
Confidence in Security: By efficiently managing compliance, CSPs convey a strong message of trust and security to stakeholders.
StandardFusion can help you build trust in your compliance journey and organization.
Request a demo to see how we can transform your compliance management into an efficient, reliable process.