Published on: Jul 28, 2022
Managing Risk and Compliance with HITRUST CSF
Although HITRUST CSF is very popular in the healthcare industry, many other organizations are implementing this framework too.
Why?
Because it's a risk and compliance-based framework that boosts overall efficiency and data protection, which is essential for every organization.
Is HITRUST the right framework for you?
This simple guide will help you understand what HITRUST is, its structure, certification process and, more importantly, if you should adopt this framework or not.
Let's get started!
HITRUST Cybersecurity Framework
The proliferation of technology left governments and regulators scrambling to develop data privacy and information security regulations. Unfortunately, due to their rapid development, many of these newly created regulations, like the Health Insurance Portability and Accountability Act (HIPAA), contained non-descript requirements open to interpretation. Consequently, this lack of clarity leaves potential gaps in information security programs across the country.
To minimize the confusion around HIPAA compliance, The Health Information Trust Alliance (HITRUST) initially established their cybersecurity framework to provide clarity to healthcare organizations regarding HIPAA compliance. As a result, organizations have since adapted HITRUST CSF to include nationally and internationally accepted security and privacy-related regulations, standards, and frameworks.
Some examples are ISO, NIST, PCI and COBIT.
What is HITRUST CSF?
HITRUST CSF plays a pivotal role in the healthcare industry. Therefore, other sectors that need to manage and safeguard sensitive data have adopted it too. Also, due to a global need for information security, organizations striving to comply with numerous regulations focus on implementing a HITRUST CSF compliant program.
Additionally, companies can improve overall efficiency and boost data protection levels by following the best practices prescribed by HITRUST CSF.
HITRUST CSF is both a risk and compliance-based framework. Moreover, it contains a comprehensive set of controls that help with:

Who should adopt HITRUST CSF?
HITRUST simplifies the data security assessment and attestation process for covered entities, including:
Healthcare providers such as doctors, dentists, and nurses.
Establishments or entities like urgent care clinics, nursing homes, hospitals, pharmacies, and their associates.
Indeed, many healthcare organizations require their vendors to be HITRUST CSF compliant and only open their doors to trustworthy vendors. Therefore, businesses that intend to work with major healthcare organizations will likely need to be HITRUST certified.
Information security is not an industry-specific issue. For instance, many organizations outside of healthcare require some assurance and are working towards HITRUST CSF compliance.
Why is this happening?
Because it is an amalgamation of best practices drawn from standards like ISO, NIST and PCI DSS.
HITRUST vs HIPAA
Diving into HITRUST CSF and HIPAA, you may be wondering:
How is HIPAA linked to HITRUST?
Are they compatible with each other?
If an organization is HIPAA compliant, does it need HITRUST certification also?
Which one is superior to the other?
As discussed earlier, HITRUST is a wider-reaching framework built upon best practices from other regulations and standards " including HIPAA.
HIPAA is a baseline to protect sensitive health information and ensure its accessibility. However, it is limited to medical professionals, vendors and others on a need-to-know basis. Furthermore, the scope of HIPAA is limited to only protecting patient information and does not impart any guidelines for overall information security.
On the other hand, HITRUST CSF is a cybersecurity framework that draws from different standards building upon existing regulations. In particular, HITRUST CSF unifies all the requirements outlined in HIPAA and other widely recognized acts and standards.
What is the goal of this integration of acts and standards?
To create a single comprehensive framework that any organization can work towards. HITRUST CSF comprises extracts from the following:
Control Objectives for Information and Related Technology (COBIT)
International Organization for Standardization (ISO)
Federal Trade Commission (FTC)
Centers for Medicare and Medicaid Services
National Institute of Standards and Technology (NIST)
Payment Card Industry Data Security Standard (PCI DSS)
Other federal and state entities
Particularly for healthcare, HITRUST CSF compliance ensures you are HIPAA compliant while providing greater security to confidential or sensitive patient information. In addition, it helps optimize security operations, reduces organizational risks, and addresses HIPAA's fundamental limitations in securing the flow of sensitive information.
HITRUST Structure
Instead of showing the full range of security controls, HITRUST defines distinct domains and control objectives. Indeed, the latest version of HITRUST v9.6.0 contains 14 control categories, comprised of 49 control objectives and 156 control specifications.
For each control, there are three levels of implementation. Level 1 is the baseline, whereas Level 3 ensures a high level of protection and includes more requirements.
Implementation Requirements provide details on the necessary controls to achieve compliance for each level. Furthermore, some requirements are industry-specific and apply to those organizations belonging to the respective industry segment.

HITRUST Certification Process
Ultimately, becoming HITRUST Certified indicates your organization's commitment to information security. As a result, it has become a benchmark for handling sensitive data with the greatest care. Also, it helps organizations, business associates, and vendors to manage risks across their third-party supply chain.
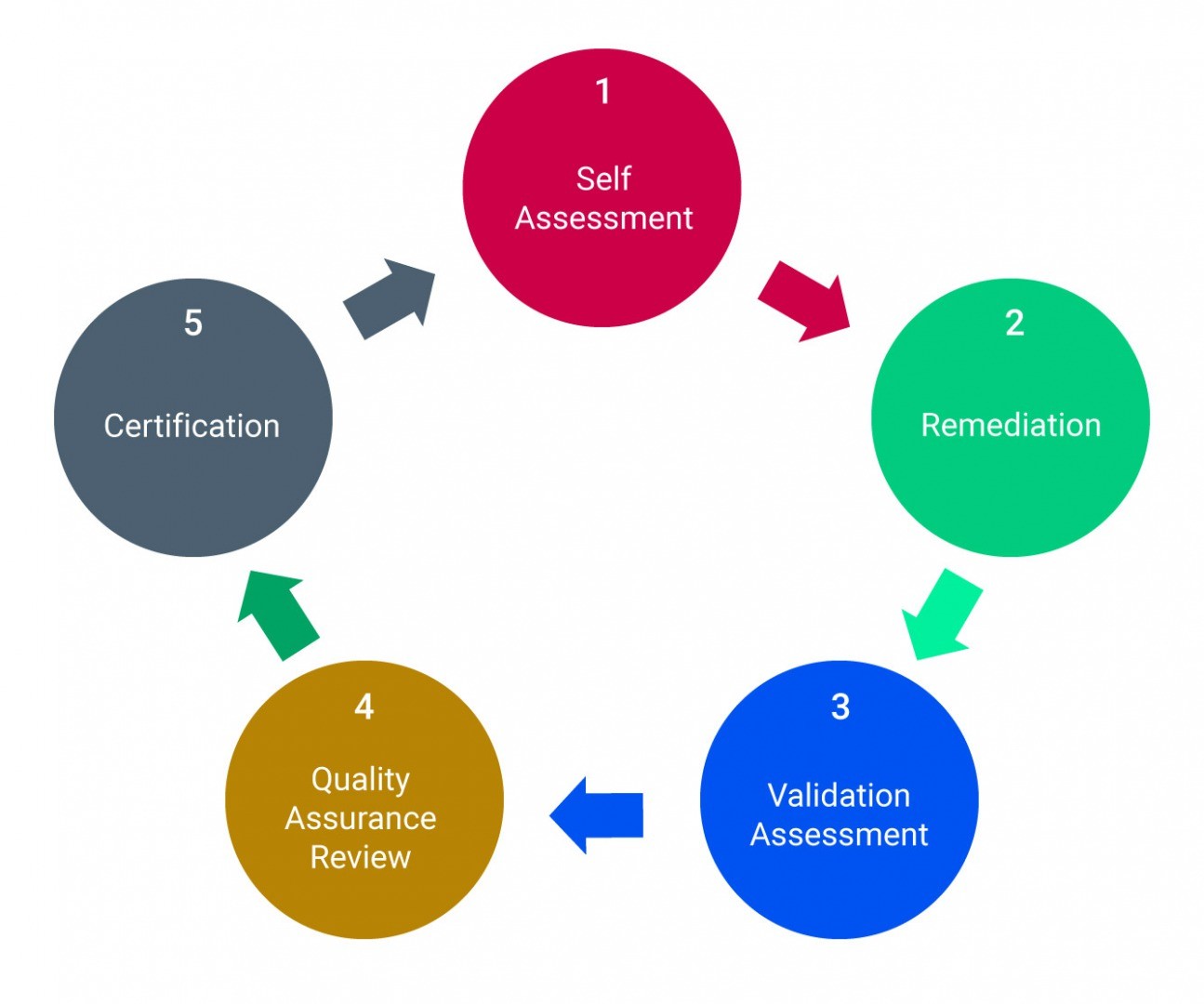
However, before the certification takes place, organizations need to prepare themselves and can perform the following:
Self-Assessment and Readiness: Organizations need to conduct risk analysis which helps in the determination of implementation level.
Remediation: Based on the risk analysis, organizations will perform remediation and patch up all risks.
Validation Assessment: CSF assessor will analyze the self-assessment reports and remediation actions performed by an organization.
Quality Assurance Review: CSF assessor will review the performance of controls and determine the satisfaction level.
Certification: A certification letter is issued if all performance controls are deemed satisfactory.
Information security regulations and data privacy acts are playing catch up, and HIPAA is no different. Unfortunately, due to its expedited development, HIPAA's compliance requirements were ambiguous, generating more confusion. As a result, HITRUST CSF was created to alleviate the uncertainty around HIPAA, acting as a foundational framework to help you create a robust risk and compliance management system.
Using GRC software like StandardFusion, it has never been easier to build and scale your organization's information security management system (ISMS). Map your controls directly to your requirements and visualize the connections between all the moving parts of your management system.







