Published on: Jul 15, 2022
How can Penetration Testing Improve your GRC Program?
The value of your organization eventually comes down to how clean, safe, and reliable your data is.
So, this is the key question: Can you trust your data?
This article will help you understand how penetration testing can provide clear and concise direction on securing your company's value from cyberattacks.
Let's get started!
What is Penetration Testing?
A penetration test is a simulated and controlled cyberattack on your organization executed by professional security experts. These penetration testers (also known as "white hat" hackers) use strategies and tools to access your computer systems, networks, websites, or applications.
Penetration testing (or pen testing) aims to identify vulnerabilities in your IT security systems, so you can repair these weaknesses before cybercriminals exploit them. Moreover, it can evaluate the performance of your organization's security programs and internal controls.
For example, you can evaluate:
Regulatory compliance
Employees' security awareness (phishing or social engineering)
As a result, pen testing reveals how cybercriminals can access sensitive data through computer systems, networks or even your employees.
The bottom line?
Penetration testing will help you uncover and quickly remediate security weaknesses, keeping you always one step ahead.
Why do you Need Penetration Testing in your GRC Program?
According to PWC, cyber risk is a top concern for CEOs in 2022 " even more than macroeconomic volatility, health risks, climate change or geopolitical crises in some cases.
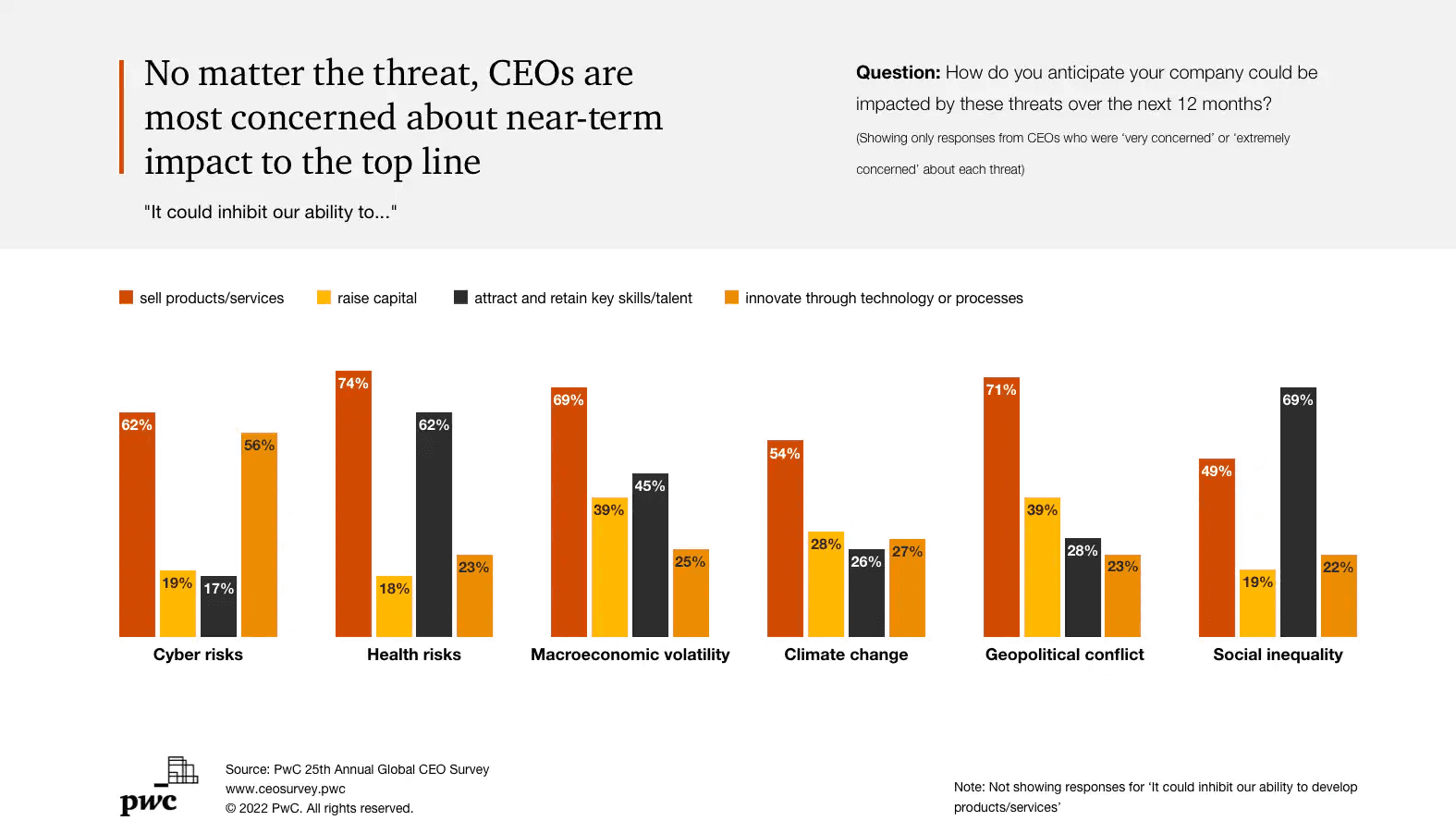
So, here is the deal...
Cybersecurity is not just spending resources and creating hundreds of policies for internal control. Instead, you must be proactive and identify security gaps through constant examination and tests.
Did you know that 2021 had the highest average data breach cost in 17 years?
IBM report shows that costs rose from USD 3.86 million to USD 4.24. Moreover, the average cost was USD 1.07 million higher in breaches where remote work due to COVID-19 was a factor.
Here is where penetration testing comes in.
Certainly, it would be best to validate your cybersecurity and internal policies in a real-world (but controlled) environment. By doing so, you will expose your organization to techniques and methods that a real hacker would employ.
Once you understand your vulnerabilities, you can improve your internal controls, assess risks more efficiently and remediate security weaknesses. As a result, you will enhance your compliance programs, generating more business and increasing trust from your clients.
Software Secured is a leading Canadian provider in offering penetration testing services for companies undergoing compliance. Learn more about their services here.
Assessing Risks with Penetration Testing
Risk assessment is a vital part of your cybersecurity management process and a requirement of many IT standards. On the other hand, pen testing is a way to assess cybersecurity risks by exposing your organization's vulnerabilities.
What does this mean?
Penetration testing has an essential role in risk evaluation. In particular, it helps you identify, assess, and prioritize your company's risks.
The following image shows the risk management process:
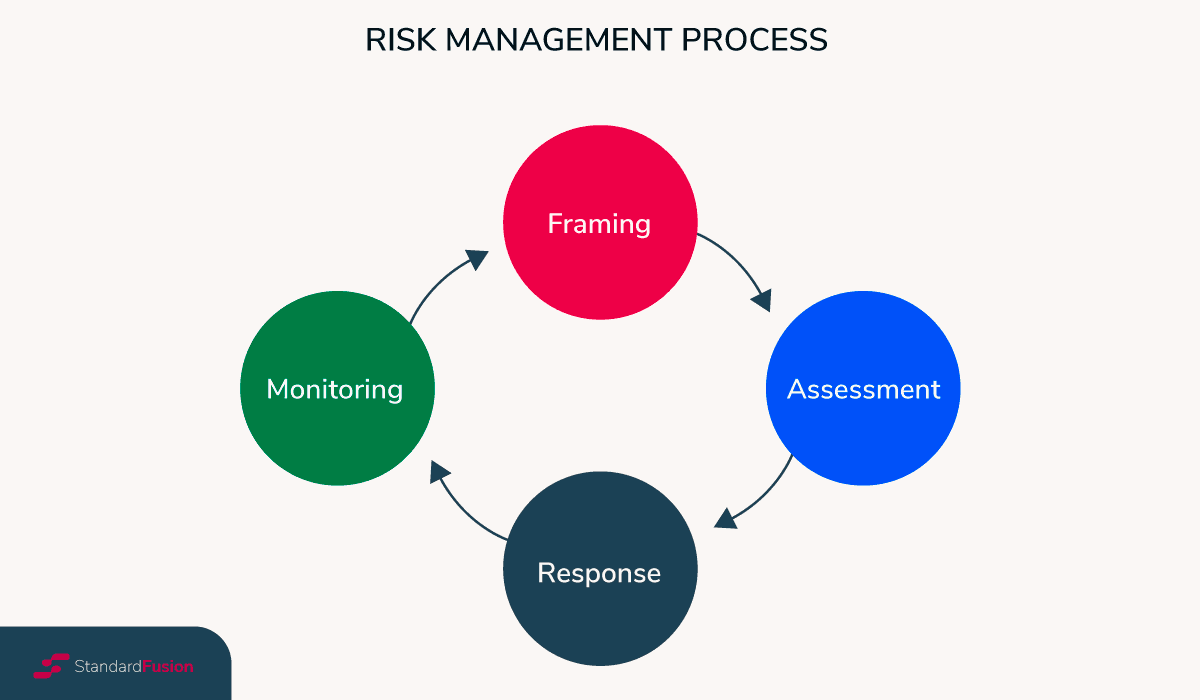
In particular, a risk assessment will help you with:
Identifying vulnerabilities, threats, and risks
Estimating the probability of risks being realized
Defining mitigation priorities by risk severity and the likelihood of occurrence
Assessing risks and threats is vital to improving your cybersecurity. In fact, it is a continuous process that helps you evaluate your security controls, identify issues, and estimate their impact.
Why conducting this assessment?
To prevent hacks, data breaches, and data loss.
Evaluate network security
To ensure compliance
Create security policies and procedures
Reallocate resources
Train your employees
Protect your reputation
There are three critical stages you must include in the assessment.
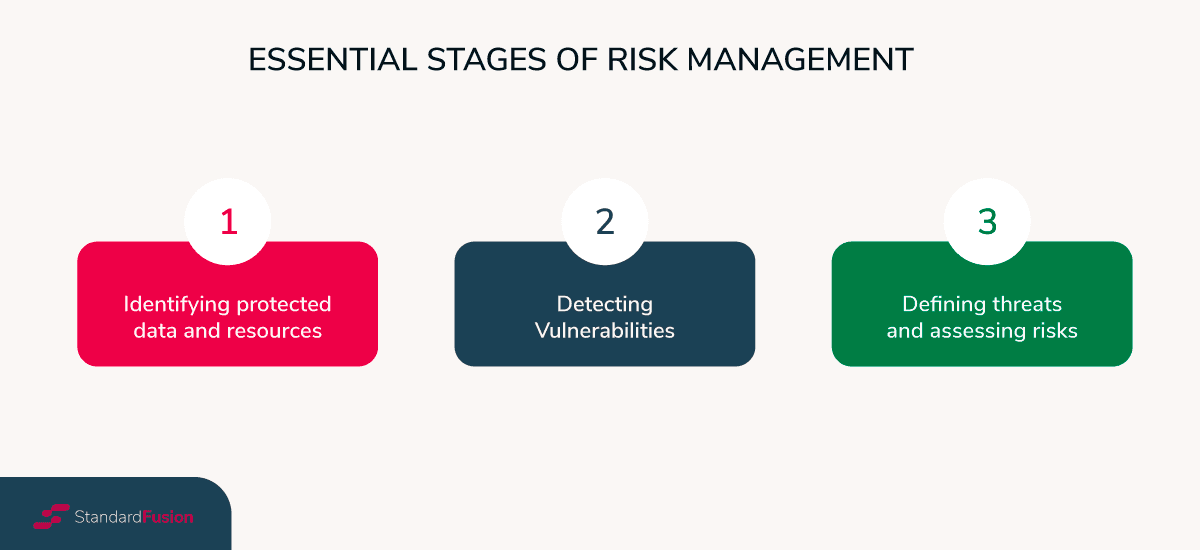
The first stage aims to list all the data and resources you need to protect. Some examples are:
Personal information of clients and employees
Financial data
Partners information
Unique business activities
The second state is detecting vulnerabilities. For example, you can use vulnerability scanning.
Finally, the third risk assessment stage is defining threats and assessing risks. Here, you need to:
Analyze vulnerabilities
Prepare for possible exploits
Estimate the likelihood of risks occurring
Assess the potential consequences
A wide range of security practices can help you with this third stage, risk assessment. However, penetration testing is the most balanced regarding time consumption, cost, risk coverage, and results. Furthermore, penetration testing is a requirement of NIST, HIPAA, PCI DSS, GDPR, SOC 2, ISO 27001, and other regulations.
How Often Should you do Penetration Testing?
Penetration tests are not a one-time activity. Instead, they have become a standard exercise for organizations to uncover weaknesses and assess their security posture. For example, most organizations conduct penetration tests 1 - 2 times yearly or quarterly (penetration testing as a service). However, many others perform these tests monthly, weekly or even daily.
So, what should you do?
Although there isn't a one-size-fits-all solution, you should run a pen test if you are:
Adding a new network infrastructure or web application
Upgrading your information systems
Moving to new offices
Applying security patches
Modifying end-user policies
Also, if you are unsure, remember that the frequency of the penetration tests also depends on:
Company size: Larger companies might have more urgency to test their systems.
Exposure: Companies with more exposure (different countries) tend to be at a higher risk.
Budget: Penetration tests are expensive so smaller organizations will test less frequently.
Compliance: Depending on the industry, you might need to run pen tests for compliance (OC 2, PCI DSS, and ISO 27001)
Infrastructure: If your company has a 100% cloud environment, you might not be allowed to test that infrastructure.
In a nutshell:
Your data determines the value of your organization. So, undoubtedly, the more tests you run, the better you will prepare your business against cyberattacks. At the very least, you should run 1 or 2 penetrations tests per year. However, if you have the opportunity, you could run penetration testing as a service.
How to Best Leverage Penetration Testing Results to Improve your GRC Efforts?
You run the test, and the results shock you " your networks are not as safe as you thought, and your data may be at risk. Also, your employees are not following some of your internal processes.
What happens next?
Well, you have just completed a successful penetration test. You are one step ahead of real hackers who want to steal your data. Moreover, the penetration testing report you will receive is a goldmine of information and evidence you need to work on immediately.
How can you leverage the results?
This is what you can do with your pen test results to improve your security posture:
1) Review and discuss the results with your team: Go over the report summary, the different tests performed and the results. In particular, you need to identify and quantify the security risks and determine the possible causes.
2) Replicate all known issues: A good penetration testing report should include everything you need to replicate each issue the testers found.
Why should you do this?
False positives can exist
Reproducing vulnerabilities will help you understand them internally
3) Rate each risk: If the penetration test results show more than one issue, you need to rate them according to severity.
4) Determine a resolution for each risk: It is time to get to work. In general, there are found major resolutions to aim for:
Eliminate: Closing the vulnerabilities
Reduce: Mitigate the vulnerabilities, reducing the likelihood of exploitation.
Manage: You know the vulnerability and monitor it (but it is not mitigated).
Accept: The vulnerability exists within your risk acceptance.
5) Implement the fixes: This step is straightforward. The developers and security experts will start implementing the solution you and the team have found.
6) Review the process: Whether this was your first or tenth pen test, evaluations and reviewing are never-ending processes.
These are some critical benefits penetration testing will bring to your GRC efforts:
Evaluates the effectiveness of security control and policies
It helps identify the effectiveness of security awareness training
It will help you identify your security posture
Provides information to support regulatory compliance
It enhances the effectiveness of your overall security lifecycle
Identifies and categorizes risks
Final Thoughts
Pen testing is a valuable part of a comprehensive security program. In fact, it can provide clear and concise direction on securing your data and networks from real-world attacks.
Most importantly, cybersecurity is more than spending resources and creating policies. It is about proactivity and long-term, constant examination and improvement of your systems and processes.
In essence:
To ensure confidentiality, integrity and availability of your data (company's value), you should regularly test your information security programs.







