Published on: Oct 4, 2023
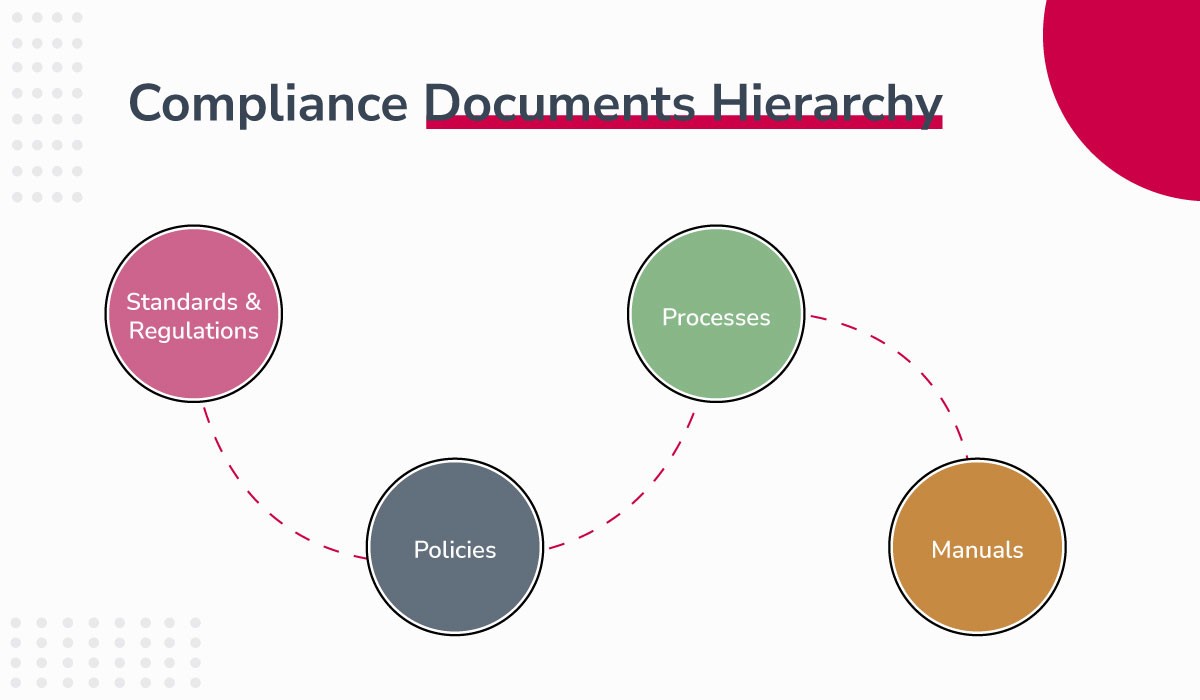
Compliance Documents Hierarchy: Standards, Policies, Processes, and Manuals
Compliance documents may sound like a dry subject, but they're the backbone of trust, security, and fairness in today's fast-paced industries.
This article will help you understand the hierarchical structure of compliance documents and learn how to implement them effectively in your organization.
Let's begin!
The Current State of Compliance
In today's fast-paced tech environment, governance is the unsung hero that has a critical role in guaranteeing fairness, security, and trust. Finance hubs, healthcare systems, and Silicon Valley startups all need one thing: structured compliance.
Let's be honest, compliance is not straightforward.
It is more like a labyrinth of acronyms, jargon, and guidelines that can make even the most seasoned professionals scratch their heads. Compliance Officers navigate this labyrinth, aligning not just their company but also multiple departments.
According to a 2022 Global Compliance Association survey, over 60% of businesses consider compliance a top challenge. So, imagine how hard it must be for all these organizations to understand the progressive hierarchy of compliance documents that are needed to guide their actions.
Let's break down the barriers of confusion. Next step: Hierarchical structure of compliance documents.
What is the Hierarchical Structure of Compliance Documents?
The hierarchical structure of compliance documents forms a well-organized framework that guides organizations in adhering to industry standards, regulations, and best practices. Moreover, this structure ensures that businesses operate ethically, securely, and within legal boundaries.
This structure dictates the order in which your documents should be developed to maintain consistency with the Compliance Program in general.
First things come first. That means starting with your Program.
Before diving into the document hierarchy, firmly set and articulate the objectives of your program. These objectives will rule everything that comes next, paving the way for subsequent documentation, ensuring everything aligns with your organization's overarching goals.
Additionally, you can start listing distinct types of documents that will need to be in place, one by one, to build your compliance foundation. Here is how you do it:
1. Standards and Regulations
At the foundation of the hierarchy lie industry standards and regulations. These are the bedrock upon which compliance is built. Standards set forth the general principles and requirements that organizations must meet. Regulations detail specific legal rules that businesses must follow. This level matters because it provides a universal baseline for compliance.
Standards and controls grow out of the expectations set by policies, defining the practical application of those policies. Think of standards as the map guiding your organization on its dream vacation toward compliance.
Examples of Internal Standards:
Customized Approach: organizations can develop their standards to align closely with specific policies and operational requirements. This allows for a tailored approach, ensuring that every aspect of the company's goals and culture is addressed.
Flexibility and Adaptation: Internal standards offer the flexibility to adjust and evolve as the organization grows or when new challenges arise.
Examples of External Standards:
Credibility and Recognition: Standards from established external entities such as ISO or ANSI provide a level of credibility and are often recognized globally. Adopting such standards can increase trust and acceptance, especially in industries where compliance and certification are crucial.
Benchmarking and Consistency: These standards offer a consistent benchmark for performance and quality, fostering industry-wide consistency and making it easier to collaborate with external partners or in international markets.
Ultimately, the choice between developing standards internally or adopting external ones depends on the specific context and strategy of the organization. Balancing both can also be an effective way to ensure comprehensive coverage of needs while maintaining industry alignment.
Regulations detail specific legal rules that businesses must follow, this informs the controls that organizations put in place to meet these standards and regulations. This level matters because both standards and regulations provide a universal baseline for compliance.
2. Policies
Policies are high-level directives that translate standards, regulations, and frameworks into an organization's specific context. Furthermore, they outline what is expected, allowed, and prohibited within the company. On this level, you will find something like "rules of behavior," ensuring consistency on how things must be done and minimizing risk.
To effectively implement these policies, standards play a crucial role. They answer the question: "How are you going to implement your policy?" Standards can be sourced from recognized external authorities or tailored to fit the unique needs of your organization. They take the guidelines set by policies and put them into actionable language, transforming abstract directives into concrete actions.
For instance, standards might specify the exact types of data that can be stored in the cloud or detail the security controls necessary to protect that data. This granular information builds on the policies, providing a clear pathway for implementation that minimizes risk and maximizes compliance.
Examples of an Information Security Policy
In the realm of information security, organizations often establish comprehensive policies to ensure the protection and integrity of their data, such as:
Hardware and Software Usage: Organizations typically define strict guidelines regarding the technology tools employees are permitted to use. For instance, the policy might state, "All employees are required to use only company-approved software and hardware. Unauthorized software installations are prohibited to prevent potential security vulnerabilities."
Data Protection and Encryption: Another critical aspect of an information security policy involves safeguarding sensitive data. A policy might stipulate, "Any data deemed confidential must be encrypted both at rest and in transit to shield it from unauthorized access or disclosure."
In essence, standards are the bridge that takes a policy's ideals and makes them real, ensuring that high-level directives translate into everyday operational practices. Policies serve as foundational elements for maintaining a secure digital environment, enabling organizations to mitigate risks effectively and protect their assets.
3. Processes
One of everyone's favorite types of document. A process ensures that day-to-day activities. These documents detail the operational procedures and workflows necessary to execute a task in compliance with a policy. In particular, they specify how tasks are executed, who is responsible, and how to handle exceptions.
Think of a procedure like a step-by-step instruction manual. It is a list of actions that must be taken to achieve the standards and implement the controls. Procedures describe the specific ways for personnel to perform activities, ensuring that tasks are executed consistently and effectively.
For example, procedures might cover topics such as:
System Hardening: Steps necessary to secure new systems against vulnerabilities.
Architecture Reviews: Detailed instructions for evaluating system design to meet required standards.
These procedures are tailored to your unique environment, providing guidance on how tasks should be performed. For instance, if you have an encryption standard, your procedures could look like this:
To ensure whole disk encryption, enable Bitlocker on Windows systems by following specific steps.
To encrypt data in transit, require authenticated network access via third-party services like Cisco AnyConnect or NordVPN. Detailed installation and configuration instructions ensure secure data transmission.
By translating standards into actionable steps, procedures guarantee consistency, accuracy, and security, making processes essential for maintaining a robust operational framework.
4. Manuals
Compliance manuals play a crucial role in translating procedures into actionable steps that individuals within an organization can easily implement. In addition, they provide a tangible and practical guide for various operational aspects, helping to ensure that every action taken aligns with the overarching compliance framework.
By understanding this framework, organizations can ensure that their policies, standards, and procedures interrelate seamlessly, functioning like peas and carrots—or perhaps, more aptly, like a well-prepared recipe where each ingredient plays a vital role in the final outcome.
How Do Controls Mitigate Risks Identified by an Organization?
When an organization identifies potential risks, the next crucial step is establishing controls to minimize these vulnerabilities. But how exactly do controls mitigate these identified risks?
Defining Controls and Standards: Controls are the actionable measures derived from organizational standards. Standards outline the overarching goals for risk management, while controls are the specific tools or methods used to achieve these goals.
Mechanisms to Mitigate Risks: Let's say an organization recognizes the risk of exposing sensitive information. A pertinent control might be to mandate encryption, safeguarding data from unauthorized access. This might involve the implementation of whole disk encryption or using a virtual private network (VPN) to protect data in transit.
Creating Control-Centric Standards: Organizations often set standards that specify which controls are necessary. For instance, in the context of cloud computing, standards might dictate specific controls aimed at securing data stored offsite, as supported by frameworks like those outlined by the FFIEC.
Comprehensive Resources: For organizations seeking to expand their understanding of different control types, consulting resources such as the Information Security Booklet can provide valuable insights and guidance.
What Is an Example of a Control in Information Security?
In the realm of information security, a control serves as a safeguard, set in motion to counter the risks pinpointed by an organization. Think of it as both a shield and a strategy designed to protect vital assets.
For instance, consider the risk associated with unencrypted sensitive data. If an organization's policy underlines the need to protect such data through encryption, the control comes into play through specific actions to curb that risk. Examples include implementing whole disk encryption or setting up a Virtual Private Network (VPN).
These controls are not arbitrarily chosen. They arise from standards that detail the specific measures required to manage and mitigate risks. The Federal Financial Institutions Examination Council (FFIEC) illustrates this by noting that standards might define which controls should counter the risks of storing data in the cloud.
By implementing controls, organizations not only address the risks they’ve identified but also create a structured approach to managing potential threats. Learn more about how common controls and GRC data models drive organizational compliance.
Why This Hierarchical Approach Matters
After this quick voyage through the layers of compliance documentation, you need to champion effective implementation.
Why? Well, it helps you with the following:
Clarity and Consistency: The structure provides a clear path from high-level principles to practical implementation, reducing confusion and promoting uniformity in compliance efforts across an organization.
Improved Communication: Tailoring guidance for specific departments is very important, but if Policies should not be customized, procedures should, and manuals must be audience-driven.
Efficiency: The structure streamlines compliance efforts by breaking down complex requirements into manageable steps, enabling efficient allocation of resources.
Transparency and Accountability: Each level of documentation fosters transparency by clearly outlining responsibilities and processes. This, in turn, promotes accountability among employees and stakeholders.
Continuous Improvement: The hierarchical approach allows for continuous improvement as owners can review, update, and refine their documents to adapt to changing requirements (internal and external).
Not following rules can cost companies about $14 million per incident, according to IBM. So, it's important to use this hierarchy to protect your company's reputation, money, and long-term success.

Challenges and Solutions in Implementing Hierarchical Compliance Documentation
Creating and developing the right documents within the hierarchical structure of compliance can seem like a daunting task, but don't worry you'll go through the process step by step. Ensuring that your organization's compliance documentation aligns seamlessly with the established hierarchy is essential for maintaining transparency and consistency.
Let's discuss how.
1. Standards and Regulations:
Top leadership should begin by identifying the relevant industry standards and regulations that apply to your organization. This will be the baseline of your Compliance Program.
Structuring these requirements and breaking them down by categories, or departments to better define ownership is non-negotiable and forms the bedrock of your compliance framework.
2. Policies and Procedures
Collaboratively develop policies with the department leaders. Policies must reflect the principles outlined in the standards and frameworks. Policies should clearly communicate what is expected, allowed, and prohibited within the organization. To enhance this process, consider leveraging policy management software. Such tools can streamline the creation, documentation, management, and export of your policies, ensuring they are comprehensive and easily accessible.
3. Processes
Work closely with employees from various departments to define the detailed processes that guide day-to-day operations. Identify key tasks, responsibilities, and decision points within each process. Utilizing software solutions can help document these processes and ensure they are aligned with your policies and standards, making updates more efficient and less disruptive.
4. Manuals:
Support employees from different levels to document comprehensive manuals that outline how to execute these processes while adhering to the established policies and procedures. Encourage a collaborative approach, involving employees who are directly involved in these processes to provide input and validation. Software tools can assist in maintaining these manuals, allowing for easy updates and version control.
Once these documents are fully developed and implemented, make sure to support the good practices with:
Document Templates (especially for processes and manuals)
Open Communication
Training and Awareness
Document Review (at least once a year)
By following these steps and involving your employees throughout the process, you can ensure that your organization's compliance documentation is not only accurate and comprehensive but also reflective of the collaborative effort to maintain a culture of compliance and integrity.
Remember, building these documents is not a one-time task, it's an ongoing commitment to excellence in every operational facet. Incorporating the right software solutions can significantly enhance your capability to manage and adapt your compliance documentation effectively.
Well-structured Compliance and Data Breaches
The key to effective implementation comes into sharp focus, backed by compelling evidence. A recent industry report by PwC revealed that organizations with well-structured compliance frameworks experience 50% fewer compliance breaches, showcasing the tangible benefits of this approach.
The path to success is illuminated by the clarity and consistency inherent in the hierarchical structure, reducing confusion and fostering uniformity in compliance efforts across departments.
By tailoring guidance while preserving the integrity of policies, procedures, and audience-driven manuals, companies can enhance communication, optimize resource allocation, and cultivate a culture of transparency and accountability among stakeholders.
Key Takeaways
Compliance is a top challenge for over 60% of businesses.
A hierarchical structure helps in organizing compliance documents effectively.
Each type of document, Standards, Policies, Processes, and Manuals, serves a distinct purpose in the compliance hierarchy.
The structured approach provides clarity, improves communication, and increases efficiency within organizations.
Customization at different levels of documentation enhances its effectiveness and applicability.
Compliance breaches can cost companies an average of $14 million per incident.
Involving employees in the documentation process helps maintain a culture of compliance and integrity.
Regular document review and open communication are essential for long-term compliance success.
Companies with structured compliance frameworks experience 50% fewer breaches.
Building and maintaining strong compliance documents is an ongoing commitment, not a one-time task.
Are you looking for a structured, step-by-step approach to compliance? Connect with our team to learn how StandardFusion helps you manage compliance with multiple standards in a single platform. StandardFusion makes it easy for you to develop and manage your documents effectively, ensuring everything aligns with your overarching organizational goals.