Published on: May 19, 2022
| Updated: Feb 27, 2025
How to Implement a VRM Program: 5 Key Tips
Implementing a Vendor Risk Management (VRM) program is essential for protecting your organization from potential threats and ensuring strong vendor relationships. A well-structured VRM program provides visibility into third-party risks, helps maintain compliance, and strengthens overall business resilience.
In this article, we’ll walk you through the key steps to establishing an effective VRM program, including five essential tips to set your organization up for success.
Why are Vendor Risk Management Programs Important?
VRM is a discipline focused on mitigating vendor risks. The program provides visibility into the vendor relationship and offers insightful guidance on how to effectively monitor vendor performances and quality (or lack of) controls during the lifetime of the business relationship.
Disruptions, ranging from supply chain shortages to brazen cybersecurity attacks on some of the largest technology or infrastructure service providers, have amplified the crippling and global effects of vendor challenges on every business.
The 2022 security data breach at Okta underscores the risks when relying on vendors to handle part of your operations. This breach occurred via one of its key vendors, a sub-processor that provides customer support services to Okta's customers.
Even though Okta reported that only 366 corporate customers were impacted (2.5% of its customer base), this is significant because thousands of companies rely on Okta to manage user authentication to networks, applications, and services. The vendor had access to Okta's internal networks, ticketing system, customer listing, and customer environments in some cases.
Regardless of the organization's size, industry or maturity, no organization is immune from the domino effects of vendor risks.
How Vendor Lifecycle Management Enhances Third-Party Risk Management
Effectively managing vendor relationships is crucial for mitigating risks, especially when relying on third parties. Vendor lifecycle management offers a structured approach that makes third-party risk management both thorough and efficient.
1. Establishing a Strong Vendor Onboarding Process
A robust vendor onboarding process is the foundation of a healthy vendor relationship. By conducting comprehensive vendor assessments, businesses can identify potential risks right from the start. Key steps include:
Due Diligence: Vet vendors through background checks, financial stability analysis, and compliance with industry standards.
Contractual Agreements: Clearly outline expectations and risk-related clauses to ensure vendors are aligned with your risk management policies.
2. Continuous Monitoring and Vendor Management
Once onboarded, vendors must be regularly monitored to ensure they maintain the standards required. This includes:
Performance Evaluation: Regularly assess vendor performance against agreed benchmarks.
Risk Assessment: Conduct periodic risk evaluations to catch any potential vulnerabilities early.
3. Effective Offboarding Practices
When a vendor's contract ends, or if they no longer meet your standards, a seamless offboarding process is vital to mitigating risks. Consider the following best practices:
Data Retrieval and Destruction: Ensure all company data is returned or securely destroyed to prevent data breaches.
Exit Interviews: Conduct exit discussions to uncover any latent issues that could inform future vendor relationships.
4. Crafting an Inclusive Vendor Management Policy
A detailed vendor management policy provides a clear framework for handling vendors throughout their lifecycle. Such a policy should include:
Roles and Responsibilities: Define who is responsible for vendor relationships at each stage.
Risk Management Procedures: Detail the steps for identifying, evaluating, and mitigating vendor risks.
Implementing these practices will not only enhance your third-party risk management but also strengthen the overall resilience of your business operations.
Launching Your VRM Program
Even though your business is not entirely immune, you have control over the magnitude of the harm caused by these events. You influence what measures you can take to reduce organizational vendor risks to an acceptable level.
Launching a VRM program from scratch is not easy. A lot comes into play and must be considered when deciding what you want the program to accomplish, how to strengthen your vendor risk management processes, and how to measure its success. You'll need to consider factors such as:
Time Commitment: Determine how much time to devote to developing and maintaining the program.
Resource Allocation: Identify what resources are required for effective implementation.
Continuous Management: Plan how to manage the program on a continual basis to adapt to evolving risks.
Whether you're trying to implement a VRM program for the first time or looking to mature some of your existing practices, taking time to evaluate and build out the program will lead to greater success. By accessing expert guidance and thoroughly planning your approach, you can significantly minimize third-party risks and safeguard your business.
Where to start? Below are five tips to provide some guidance and inspiration on your journey.
Tip #1: Align Business Goals With The VRM Program
Start off by understanding what goals you want to achieve and use these factors to create a game plan. This holistic approach will help clarify and prioritize the top risks to mitigate (e.g., cybersecurity, strategic, and regulatory risks), enabling you to prioritize what needs to get done. Not all vendor risks will be treated equally, as the industry your organization operates within will determine what you need to prioritize.
At the minimum, create a vendor risk management playbook that lays out high-level guidance. This will be a handy resource for your company as you build and mature the program.
Key aspects to include in the playbook:
Purpose: Identify your goals for the VRM program (the "why");
Roles and Responsibilities: Identify key stakeholders and their specific responsibilities (the "who");
Risk Categories: Identify key vendor risks to your organization (the "what");
Vendor Lifecycle: Identify relevant stages of the vendor lifecycle to consider. The phases may include procurement, continuous monitoring, and offboarding (the "when");
Vendor Management Activities: Identify the activities to be performed during the varying stages of the lifecycle (the "how").
Your VRM program will evolve, so it's essential to keep it current by reviewing the plan at least annually. And as needed, make updates to the playbook to proactively address changing dynamics.
Understand the Types of Vendor Risks
To effectively manage vendor risks, it's crucial to recognize the different types that can impact your organization. Here are the eight primary categories of vendor risk:
Cybersecurity Risks: Threats related to data breaches and cyber-attacks.
Compliance Risks: Issues arising from non-adherence to regulatory standards.
Operational Risks: Disruptions to your business operations caused by vendor failures.
Reputational Risks: Damage to your organization's reputation due to vendor actions.
Financial Risks: Financial losses resulting from vendor instability or failure.
Strategic Risks: Misalignment of vendor services with business objectives.
Geopolitical Risks: Risks associated with vendors operating in volatile regions.
Fourth-party Risks: Risks arising from your vendors' subcontractors.
Quick Wins for Managing Vendor Risks:
Conduct Thorough Vendor Assessments: Evaluate vendors based on specific risk categories relevant to your organization.
Implement Continuous Monitoring: Regularly track vendor performance and compliance to catch issues early.
Develop Incident Response Plans: Prepare for potential vendor-related incidents with clear, actionable plans.
Foster Strong Vendor Relationships: Maintain open communication and collaboration with vendors to address risks proactively.
By combining these insights with a robust VRM program, your organization will be well-equipped to identify, assess, and manage vendor risks effectively.
Tip #2: Create Standardized Agreements
A standard set of agreements can help your organization grow. It can also increase efficiency by saving time on drafting, negotiating, and signing. Some large vendors insist on using their own templates. However, this baseline will help lower legal costs and save time in negotiating contracts.
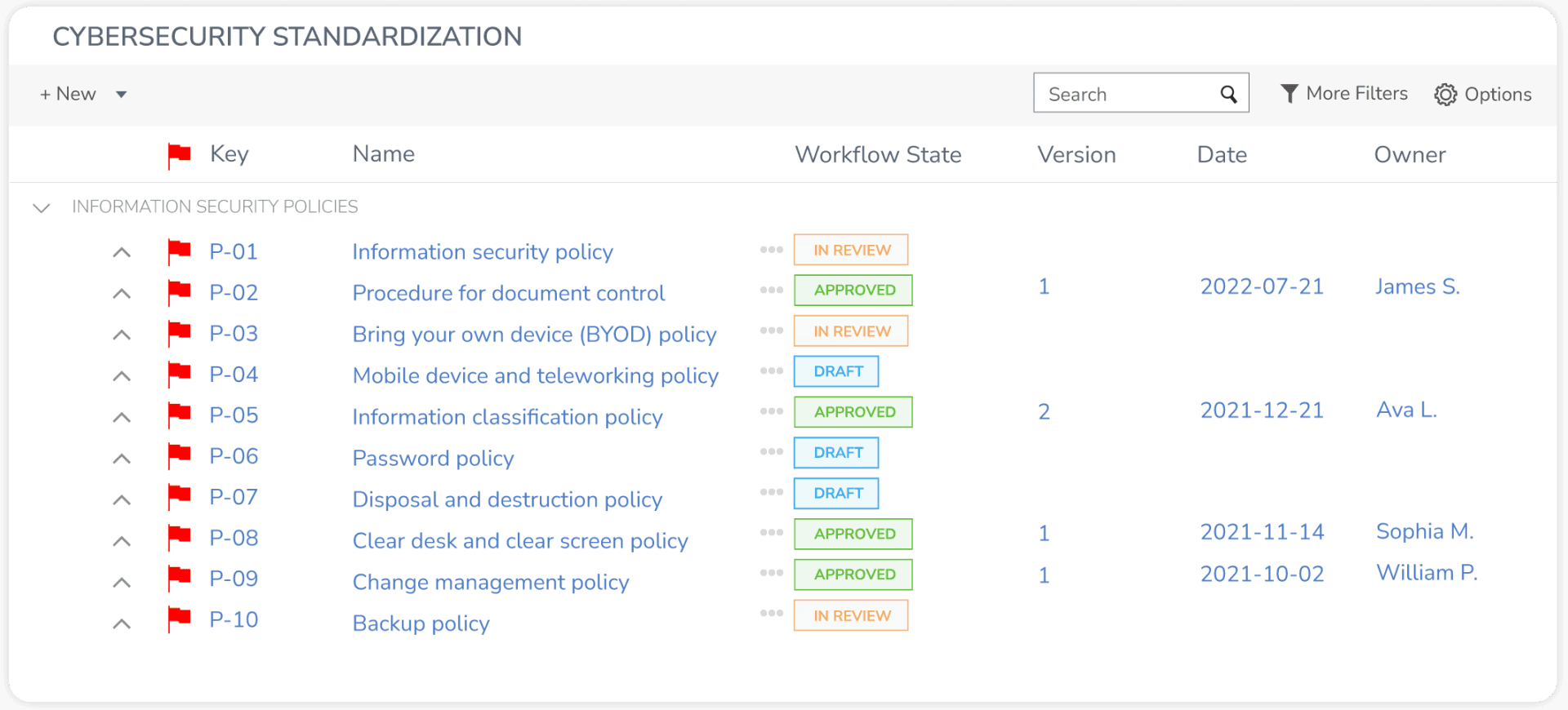
The following elements should be included:
Vendor Service Agreement: Defines the terms and conditions of the purchase of goods or services. Include these details in the contract: scope of services or goods to be covered, the timing of services, payment terms, party's responsibilities, renewal and termination, indemnification, and enforcement clauses.
Security Addendum: Establishes cybersecurity practices and protection measures to which service providers should adhere. This may include: audit or certification requirements, data encryption and key management, access controls, endpoint security, hardening standards, monitoring/logging protocols, vulnerability detection and management, governance practices, and incident detection and response.
Data Processing Agreement (DPA): DPA is a legal contract between a data controller and a data processor that outlines the responsibilities and obligations of each party concerning how to process the data. It sets out the measures to be taken to ensure the security and confidentiality of the data, and compliance with relevant data protection laws and regulations.
Depending on your organization's expertise, engaging outside legal counsel and cybersecurity subject matter experts to help with designing these requirements is worth every penny. These templates will set the tone for future negotiations and mitigate unnecessary pain points during the procurement process.
Tip #3: Implement a Well-Defined Vendor Selection Process
Creating a consistent approach to vetting vendors helps to identify the ideal vendors by asking the right questions at the beginning. Conducting a thorough vendor risk assessment and selection process is also vital for safeguarding your organization against potential threats.
Here are the critical steps to follow during the vendor selection process:
1. Vendor Information and Background
Company Overview: Start by gathering basic details about the vendor, such as their headquarters location, number of employees, and years in business.
Financial Stability: Assess the vendor's financial status to ensure they have the resources to meet commitments and withstand economic fluctuations.
2. Compliance and Regulatory Requirements
Regulatory Compliance: Confirm that the vendor complies with relevant industry standards and regulations, such as GDPR, HIPAA, or PCI DSS.
Certifications and Audits: Review any certifications they hold, such as ISO/IEC 27001 or SOC 2, and check their audit history for any red flags.
3. Data Security Measures
Data Protection Policies: Evaluate how the vendor handles and protects data, including their encryption methods and access controls.
Incident Response Plan: Ensure they have a well-documented incident response plan to address potential data breaches swiftly.
4. Risk Management Practices
Risk Profile: Understand the risk profile of the vendor and their approach to managing risks, such as risk assessments and mitigation strategies.
Third-party Dependencies: Examine any subcontractors the vendor relies on, as they can introduce additional risks.
5. Operational Resilience
Business Continuity Plans: Verify the existence of robust business continuity and disaster recovery plans to maintain service delivery during disruptions.
Performance History: Review their previous performance records and client feedback to gauge reliability and effectiveness.
6. Contractual Obligations and Service-Level Agreements (SLAs)
Contract Review: Analyze the contract thoroughly, focusing on terms related to data security, confidentiality, and termination clauses.
SLAs: Ensure SLAs are clearly defined, covering uptime guarantees, response times, and penalties for non-compliance.
7. Vendor Relationships and Communication
Management Structure: Understand the vendor's management structure to know who to contact in various situations.
Communication Practices: Evaluate their communication practices to ensure they align with your organization's needs for transparency and responsiveness.
By addressing these key areas, your vendor risk assessment report will provide a detailed overview of potential risks, enabling better decision-making and stronger partnerships.
Tip #4: Vendor Onboarding and Offboarding
A critical component of your VRM program is effective vendor onboarding and offboarding. These processes not only facilitate smooth transitions but also ensure compliance and risk reduction throughout the vendor lifecycle.
Benefits of Vendor Onboarding:
Risk Mitigation: Proper onboarding practices help identify potential risks early, reducing the likelihood of security breaches or compliance issues.
Efficiency: Streamlined processes lead to quicker integration of vendors into your operations, minimizing downtime.
Relationship Building: Establishing clear expectations and communication channels fosters a strong vendor relationship from the start.
Best Practices for Vendor Onboarding:
Due Diligence: Conduct thorough background checks and assess the vendor's compliance with industry standards.
Clear Communication: Set expectations upfront regarding deliverables, timelines, and responsibilities.
Documentation: Maintain comprehensive records of all agreements and evaluations for future reference.
Best Practices for Vendor Offboarding:
Risk Reduction: Proper offboarding minimizes security risks by ensuring that access credentials are revoked, and data is securely transferred or deleted.
Knowledge Transfer: Document and transfer any critical knowledge to avoid disruptions to your operations.
Feedback Loop: Use offboarding as an opportunity to gather feedback that can improve future vendor interactions.
By following these best practices in your VRM program, you can improve your vendor management strategy. This will ensure that onboarding and offboarding processes are effective. Keep these steps front and center in your playbook to navigate the dynamic landscape of vendor relationships effectively.
Tip #5: Perform Periodic Vendor Assessments
There must be a level of trust when you first engage a vendor. Since vendor dynamics and cybersecurity posture may change over time, reviewing your vendors periodically is imperative.
This will confirm they are providing services as expected. There is a system to monitor for poor performance or cybersecurity issues. This helps catch problems before they risk your business.
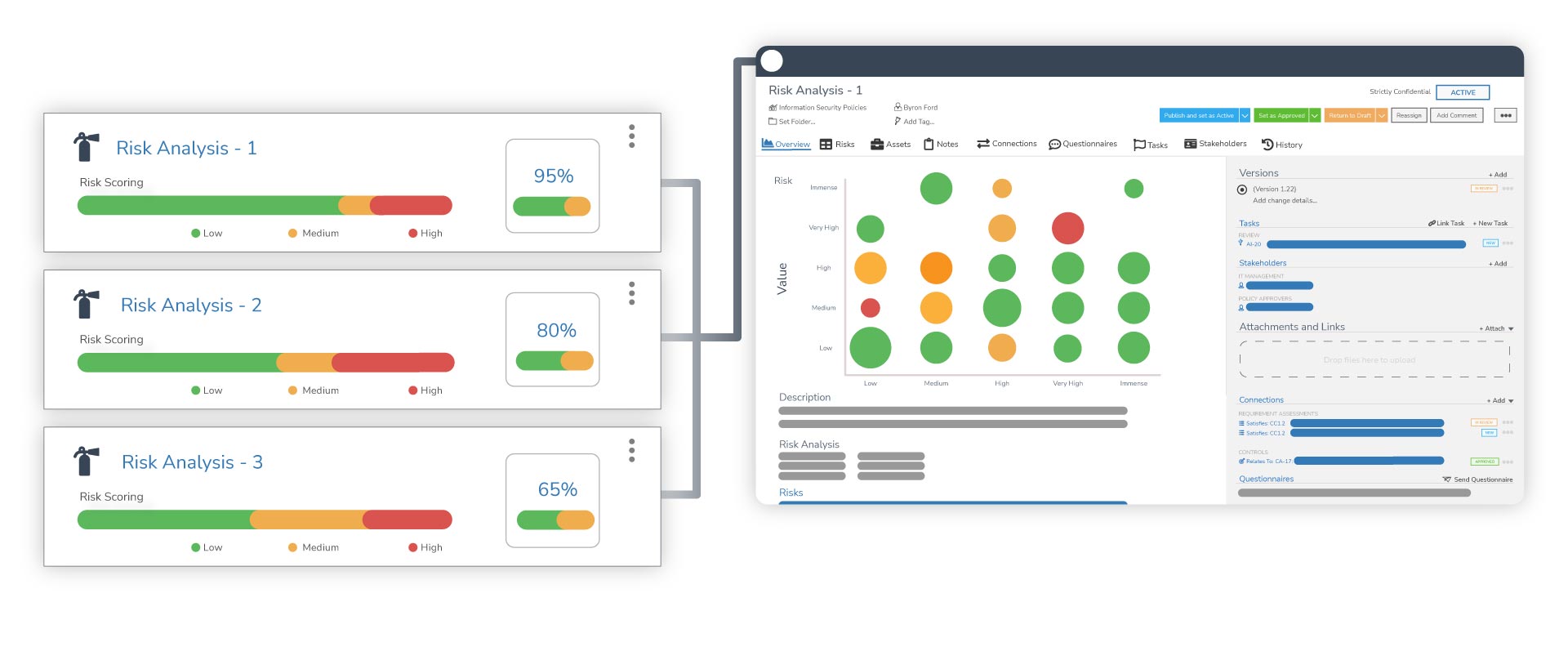
Incorporating a structured approach to vendor risk assessment is crucial, as outlined in various guides and resources. Here are the steps you should consider for a comprehensive evaluation:
Step 1: Catalogue and Classify the Vendors:
First step (catalogue): Compile a listing of your key vendors to be reviewed. Documentation is vital because you can't assess or even protect something if you don't know what you have. Start by documenting some basic information for the vendors, such as indicating what service(s) they provide, the type of data they have access to, the level of integration with your business, the contract duration, existing compliance frameworks or regulations they need to follow, and other business factors deemed important.
Second step (classify): Assign a risk level to each vendor based on your internal ranking system. For instance, your decision matrix may state that all vendors with access to sensitive customer data or your databases would be considered "high risk" (aka access to the "crown jewels"). In contrast, vendors with non-administrative system access may be "moderate risk," and vendors with no access to any corporate systems would be classified as "low risk."
Step 2: Conduct Security Reviews
Effective vendor security reviews are vital for maintaining a secure partnership. These reviews should include:
Audit Reports: Examine current audit reports such as SOC 2, ISO27001, or PCI DSS to ensure compliance.
Risk Questionnaires: Utilize internally designed or online assessment questionnaires like CAIQ or SIG to gauge vendor security posture.
Security Audits: Perform vendor security or compliance audits to validate their security claims.
Step 3: Determine Review Frequency
The timelines will vary across vendors. You would want to rank vendors according to their business criticality and the sensitivity of the information they handle. A general rule of thumb: the greater the level of access or integration, the more comprehensive and frequent the reviews should be.
Taking a risk-intelligent approach will optimize your resources where it's most crucial. Best practices suggest the following frequency for vendor reviews based on their assigned risk levels:
High risk: Annually (typically);
Medium risk: Every 1 to 2 years;
Low risk: Every 2 to 3 years.
Step 4: Assign Review Responsibilities
Vendor service performance reviews should be performed by the stakeholders who engaged the vendor. They would be in the best position to assess whether or not the vendor delivered on expectations.
Cybersecurity reviews are technical. They should be done by people with strong knowledge of information security, as experts understand different information security management systems (ISMS) and compliance frameworks. This task is typically assigned to the Information Security or Compliance teams in large enterprises. In smaller organizations, this may be delegated to the IT team.
By using these steps with regular vendor assessments, you create a clear and thorough evaluation process. This helps protect your business from possible vendor-related risks.
Illustrative Template:
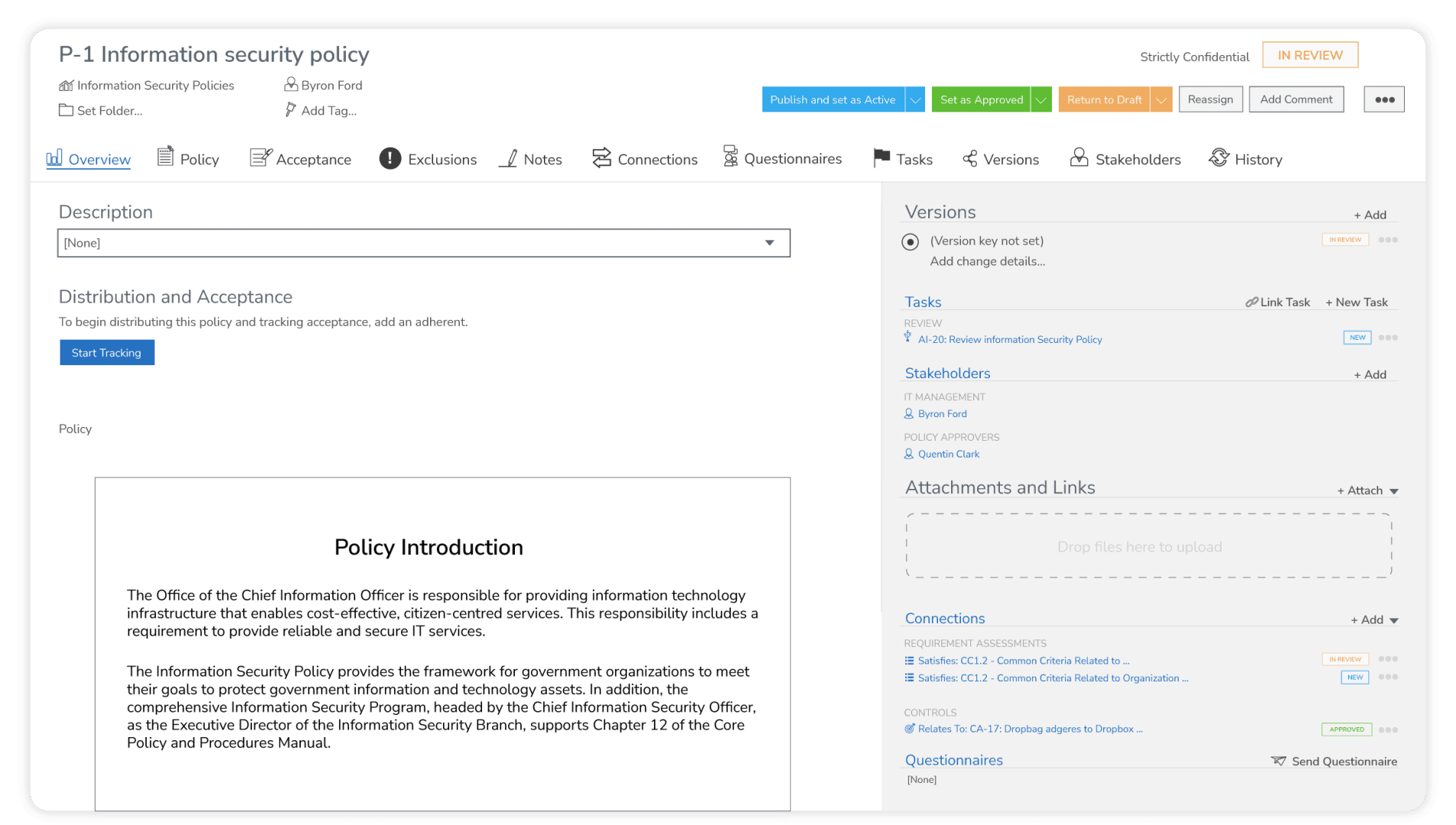
Crucial Elements to Cover in a Vendor Risk Assessment Report
Conducting a thorough vendor risk assessment is vital for safeguarding your organization against potential threats. Here’s a comprehensive guide to the essential elements you should cover to create a robust report:
1. Vendor Information and Background
Company Overview: Start by gathering basic details about the vendor, such as their headquarters location, number of employees, and years in business.
Financial Stability: Assess the vendor's financial status to ensure they have the resources to meet commitments and withstand economic fluctuations.
2. Compliance and Regulatory Requirements
Regulatory Compliance: Confirm that the vendor complies with relevant industry standards and regulations, such as GDPR, HIPAA, or PCI DSS.
Certifications and Audits: Review any certifications they hold, such as ISO/IEC 27001 or SOC 2, and check their audit history for any red flags.
3. Data Security Measures
Data Protection Policies: Evaluate how the vendor handles and protects data, including their encryption methods and access controls.
Incident Response Plan: Ensure they have a well-documented incident response plan to address potential data breaches swiftly.
4. Risk Management Practices
Risk Profile: Understand the risk profile of the vendor and their approach to managing risks, such as risk assessments and mitigation strategies.
Third-party Dependencies: Examine any subcontractors the vendor relies on, as they can introduce additional risks.
5. Operational Resilience
Business Continuity Plans: Verify the existence of robust business continuity and disaster recovery plans to maintain service delivery during disruptions.
Performance History: Review their previous performance records and client feedback to gauge reliability and effectiveness.
6. Contractual Obligations and Service-Level Agreements (SLAs)
Contract Review: Analyze the contract thoroughly, focusing on terms related to data security, confidentiality, and termination clauses.
SLAs: Ensure SLAs are clearly defined, covering uptime guarantees, response times, and penalties for non-compliance.
7. Vendor Relationships and Communication
Management Structure: Understand the vendor's management structure to know who to contact in various situations.
Communication Practices: Evaluate their communication practices to ensure they align with your organization's needs for transparency and responsiveness.
By addressing these key areas, your vendor risk assessment report will provide a detailed overview of potential risks, enabling better decision-making and stronger partnerships.
Key Takeaways
VRM is a discipline focused on mitigating vendor risks.
Disruptions caused by vendor challenges can have crippling effects on businesses.
Launching a VRM program from scratch is not easy, but it's essential to control the magnitude of the harm caused by vendor risks.
Align business goals with the VRM program to create a game plan that clarifies and prioritizes the top risks to mitigate.
Create standardized agreements to help your organization scale your requirements and increase efficiency.
Implement a well-defined vendor selection process to identify the ideal vendors by asking the right questions at the beginning.
Establish vendor performance and quality controls during the lifetime of the business relationships.
Continuously monitor and assess vendor risks ensuring that the program remains relevant and effective.
Provide regular training to employees to enhance their awareness of vendor risks and how to mitigate them.
Collaborate with vendors to achieve mutual benefits and ensure that they are aware of your expectations and requirements.







