Published on: Mar 16, 2021
| Updated: Mar 5, 2025
Crafting an Information Security Risk Register: The Essential Guide
This essential guide will help you understand how to develop and maintain a comprehensive, actionable information security risk register. The goal is to ensure your organization is not just prepared for potential threats but also ahead of them.
A key thing to remember here is that with a well-structured risk register, you'll transform challenges into a manageable, strategic advantage.
Let's begin.
What is An Information Security Risk Register?
An Information security risk register (or simply "risk register") is a strategic log that lists all potential threats that could impact an organization's operations, reputation, and compliance posture.
It's the cornerstone document that guides you through the complexity of risks. Also, it enables a clear overview of the threat landscape and a structured response strategy.
This indispensable tool goes beyond mere documentation though. It organizes and prioritizes risks, from cyberattacks to compliance slip-ups, ensuring that your organization has a plan of action ready for each
It's about transforming the unpredictable nature of cybersecurity into a structured, manageable framework.
Why Do You Need a Risk Register?
An information security risk register is indispensable in cybersecurity for its role in preemptive threat management. It provides a structured and clear approach to identifying potential risks, enabling your organization to prepare and respond effectively.
It's a tool that keeps you one step ahead, ensuring that when threats emerge, they are neither unexpected nor unmanageable. With a risk register, you're not reacting in the moment; you have a predetermined plan that can be swiftly executed, reducing downtime and mitigating damage.
Moreover, a risk register is crucial for compliance. It helps you align with industry regulations and frameworks, demonstrating due diligence and safeguarding your company's reputation. It's about having a comprehensive overview of your risk landscape and the assurance that you're ready to handle challenges head-on.
In a nutshell, an information security risk register equips GRC professionals with the following:
Pinpoint and monitor potential threats that could disrupt your organization's trajectory.
Strategically prepare for major risks to empower your team with effective response strategies.
Assess and determine the significance of each risk to decide on the appropriate course of action or inaction.
Execute comprehensive mitigation strategies to manage and minimize risks, ensuring they're maintained at a tolerable threshold.
Help you protect your organization's assets, reputation, and future in a proactive and informed manner.
Alignment with industry regulations
What Do You Include in an Information Security Risk Register?
A well-constructed information security risk register is not just a list " it's a strategic map of potential threats and your planned defenses. It should encompass the following key elements:
1. Risk Identification
Assign each risk a unique identifier, a name or code, that serves as an anchor point for tracking. This identifier organizes risks into a systemized framework, simplifying navigation and management across the organization's various facets.
2. Risk Description
Offer a concise yet informative snapshot of each risk, detailing its nature and why it's been flagged as a potential threat. This clarity is vital for understanding the gravity and nuance of each risk.
3. Risk Category
Classify risks to streamline the process of risk management. Categories could be department-specific, such as HR or IT, or type-specific like strategic or compliance risks. This classification aids in the delegation of mitigation responsibilities and enhances organizational response strategies.
4. Risk Ownership
Clearly attribute each risk to a designated custodian. This individual or team is tasked with the stewardship of the risk, overseeing its assessment, and spearheading the response strategy.
5. Risk Probability
Quantify the likelihood of each risk eventuating, using a scale or categorical system ranging from 'highly unlikely' to 'very likely'. This metric is crucial for prioritizing risks and allocating resources efficiently.
6. Risk Impact
Evaluate the potential severity of the risk's consequences on your organization. Utilize a grading scale that spans from 'extremely low' to 'extremely high' impact, providing a straightforward method for stakeholders to assess the criticality of each risk.
7. Risk Priority
Synthesize probability and impact ratings to determine the urgency of each risk. A numerical or tiered scale can help in sorting risks into a prioritized order, guiding the sequence and intensity of your response efforts.
8. Risk Response
Detail your planned countermeasures for each risk in the form of a mitigation strategy. This blueprint should be comprehensive, actionable, and clearly communicated to ensure readiness for execution.
9. Risk Status
Monitor and update the current state of each risk, classifying it as 'active', 'in-progress', 'ongoing', or 'resolved'. This dynamic status report helps track the lifecycle of each risk and the effectiveness of response actions.
10. Notes
Maintain a section for supplementary information such as historical data, related incidents, or observations that provide additional context or support decision-making regarding the risk.
By integrating these components into your risk register, you transform it into a powerful, living document that not only charts out potential hazards but also serves as a navigational tool for your cybersecurity strategy.
Understanding Information Security Risk: The Breakdown
Information security risk can be dissected into two fundamental components: threats and vulnerabilities. Together, they paint a comprehensive picture of how such risks arise and impact an organization.
Vulnerabilities: The Weak Links
Vulnerabilities are the inherent weaknesses or flaws that exist within a system. These can be software bugs that hackers exploit or even physical security lapses like misplaced sensitive documents. Human errors, such as falling for phishing scams, also constitute vulnerabilities because they present opportunities for exploitation. Ultimately, they are the doorways through which data integrity, confidentiality, and availability can be compromised.
Threats: The Catalysts of Compromise
Threats emerge when someone or something exploits these vulnerabilities. For example, when a hacker takes advantage of a software weakness to breach a system or when a deceptive email tricks an employee into revealing confidential information. In essence, threats are the actions that lead to data breaches and other security incidents.
Information Security Risks: The Consequence
When a threat successfully targets a vulnerability, it results in information security risk. This encapsulates the negative impact on an organization's data, which could range from financial losses to reputational damage. Understanding how vulnerabilities and threats contribute to these risks is key to devising effective security strategies.
By internalizing how threats and vulnerabilities interplay to create risks, organizations can better tailor their defenses to safeguard sensitive information.
Understanding Vulnerabilities in Information Security
Vulnerabilities in information security are weaknesses that can be taken advantage of to breach systems, steal data, or disrupt operations. They are diverse in nature, ranging from technological issues to human errors. Here are some common examples:
Software Vulnerabilities
Outdated Software: Applications and operating systems that are not regularly updated can contain bugs or design flaws that malicious actors can exploit.
Unpatched Security Holes: Known security gaps in software, if left unpatched, can provide hackers with easy access to sensitive data.
Network Vulnerabilities
Weak Wireless Encryption: Networks without strong encryption can be intercepted, allowing unauthorized users to access private information.
Open Ports: Unmonitored or unsecured open ports might serve as entry points for attackers.
Physical Vulnerabilities
Unsecured Devices: Laptops without proper locking mechanisms can be stolen, leading to potential data breaches.
Human Oversight: Simple actions like leaving files in public places or losing USB drives containing sensitive information pose significant risks.
Human Vulnerabilities
Phishing Attacks: Deceptive emails and websites that trick individuals into revealing passwords or financial information.
Weak Password Practices: Using predictable passwords or failing to update them regularly increases the risk of unauthorized access.
Social Engineering
Manipulative Tactics: Attackers may exploit human psychology by posing as legitimate resources to extract confidential information.
In essence, vulnerabilities can be technological or human-based, and addressing them requires a comprehensive strategy that includes regular updates, training, and robust security protocols.
How Do Vulnerabilities, Threats, and Security Risks Interconnect?
When discussing information security risks, it's crucial to understand the interconnected roles of threats and vulnerabilities. These elements form the backbone of how risks materialize in a digital environment.
Vulnerabilities: Think of these as weak points in your defensive armor. They are flaws, often found in software or processes, that attackers can exploit. Examples include unpatched software, outdated systems, or even human errors like susceptibility to phishing attacks. Without vulnerabilities, threats have no entry point.
Threats: These are actions or events that exploit vulnerabilities. For instance, when a cybercriminal discovers an unpatched software flaw, the potential for misuse becomes a threat. Phishing scams taking advantage of inattentive users are another example of threats in action.
Information Security Risks: This is the culmination of threats exploiting vulnerabilities. They represent the negative outcomes, such as data breaches or financial loss, when threats are successfully executed. For example, a hacker who successfully phishes an employee can access sensitive data, leading to reputational and regulatory consequences.
What is the Flow of Risk?
Identify Vulnerabilities: Spot potential weaknesses.
Recognize Threats: Be aware of how these weaknesses could be exploited.
Assess Risks: Understand the possible consequences if a threat succeeds.
This cycle illustrates why addressing vulnerabilities and preparing for threats is paramount. By doing so, organizations can mitigate the risks that threaten their digital landscape.
How to Create an Information Security Risk Register
Creating a robust cybersecurity risk register is a vital step towards safeguarding your organization's digital assets. Here's a strategic framework for developing one that aligns with industry best practices:
1. Uncovering potential threats:
Begin by identifying the possible risks that could impact your organization. This proactive scan should encompass:
Operational Risks: Issues that could disrupt day-to-day business activities.
Financial Risks: Threats with potential monetary losses.
Reputational Risks: Events that could harm the organization's public image.
Strategic Risks: Challenges to the company's long-term objectives and success.
Compliance Risks: Legal and regulatory non-compliance issues.
Collaboration with various team members and stakeholders is essential to ensure a comprehensive risk identification process.
2. Describe the risks
Craft a succinct yet detailed profile for each identified risk. These profiles should communicate the nature of the risk and its potential repercussions on the organization, providing clarity on the threats and their significance.
3. Evaluate risk severity
Assess the seriousness of each risk by establishing a rating system:
Highly Unlikely: Remote chance of occurrence.
Unlikely: Not expected but possible.
Likely: Could occur at some point.
Highly Likely: Expected to occur in due course.
This risk probability rating is coupled with a risk analysis scale that measures potential impact levels from 'Extremely Low' to 'Extremely High'. Consider various risk assessment methodologies to refine your understanding of each threat.
4. Prioritizing Risks
With the severity ratings in hand, prioritize risks based on their potential to affect operations. Develop a risk priority scale that combines probability and impact ratings, aiding in the allocation of resources and attention.
5. Create a response strategy
One of the core elements of your information security risk register is the response strategy. Determine how you'll tackle each risk whether by acceptance, mitigation, transfer, or avoidance and document the specific actions required for each scenario.
6. Ensure you have risk owners
Assign a risk owner to each entry, who will take charge of managing the risk and its response. This ensures accountability and clarity in the risk management process.
7. Additional notes
Include a section for additional notes to provide further context or supplementary information for each risk, which can be invaluable for understanding and managing the risk more effectively.
Maintain your risk register in an accessible format and update it regularly to reflect the evolving risk landscape. Regular reviews, potentially on a quarterly or biannual basis, will ensure the register remains current and relevant.

What Are The Common Challenges and Pitfalls of Creating an Information Security Risk Register?
Creating an information security risk register is a critical task, but it's not without its challenges and potential pitfalls. Here are some common obstacles to watch out for:
Overlooking Risks: It's easy to miss less obvious or emerging risks. Ensuring a comprehensive risk identification process that includes input from various departments can mitigate this.
Under or Overestimating Risks: Misjudging the probability or impact of risks can lead to misallocated resources. Regular reviews and updates can help maintain accuracy.
Stagnant Information: A risk register should be a living document. Failure to update it regularly can render it obsolete as new threats emerge and existing threats evolve.
Insufficient Detail: Vague descriptions can lead to confusion and inadequate responses. Clearly defined risks ensure everyone understands the threat and knows how to respond.
Lack of Ownership: Without clear risk ownership, accountability is diluted, and risks may not be managed effectively. Assigning and communicating ownership is crucial.
Inconsistent Assessment: Without standardized criteria for rating risks, assessments can vary widely, leading to an inconsistent and unreliable register.
Failure to Align with Business Objectives: If the risk register isn't aligned with the organization's goals and objectives, it may fail to protect the most critical assets adequately.
Inadequate Response Planning: Not having a clear, actionable response for each risk leaves an organization vulnerable when threats materialize.
To avoid these pitfalls, involve the right stakeholders, apply consistent risk assessment criteria, and ensure the risk register is integrated into your organization's broader risk management and business strategy. Regular training, reviews, and updates will keep your risk register relevant and effective.
How Does Human Error Contribute to Information Security Risks?
Human error is a significant factor that can compromise information security. Simple actions, like sending an email to the wrong recipient or attaching an unintended file, might seem minor but can lead to significant data breaches.
Why does this happen? It's important to recognize that everyone makes mistakes—it's part of being human. However, when it comes to safeguarding sensitive information, even small oversights can have large consequences.
Factors Leading to Security Risks
Lack of Awareness: Employees may not fully understand the importance of protecting sensitive information due to inadequate training.
Ignoring Security Protocols: If staff aren’t familiar with the organization’s policies and procedures, they’re more likely to bypass them, intentionally or not.
Overloading Information: A high volume of data and communications can lead to errors, like emailing the wrong file because of similar filenames.
Prevention Measures
Regular Training: Ensure that all employees, regardless of their role, receive comprehensive training about information security practices.
Clear Policies: Develop straightforward security protocols that are easy to follow and widely accessible to all team members.
Double-Check Processes: Encourage a culture that promotes reviewing and confirming emails and attachments before they are sent.
By being aware of these common pitfalls and proactively addressing them, organizations can significantly reduce the risks posed by human error in information security.
How to Maintain a Risk Register
Maintenance is crucial for the risk register to remain an effective tool in your cybersecurity arsenal. Here's how to ensure your risk register stays up-to-date and functional:
Regular Review Cycles: Establish a schedule for periodic reviews of the risk register. Depending on the volatility of your threat environment, this could be monthly, quarterly, or semi-annually.
Dynamic Updating: As new risks are identified or existing risks evolve, update the register immediately. This ensures the register reflects the current risk landscape.
Engage Stakeholders: Regularly involve risk owners and key stakeholders in the review process to gain diverse perspectives and insights.
Reassess Risk Ratings: As your business environment and external threats change, reassess the probability and impact of your risks to ensure accurate prioritization.
Track Mitigation Efforts: Monitor the progress of risk mitigation actions. If the actions are not effectively reducing risk, reassess and adjust your strategies.
Align with Business Objectives: Regularly align your risk register with the organization's objectives and strategies to ensure it supports business goals.
Audit and Compliance Checks: Use audits and compliance checks to verify that the risk controls are in place and effective, adjusting the risk register as necessary based on findings.
Training and Awareness: Continuously educate and train your team about the risk management process and their roles within it to maintain a risk-aware culture.
Leverage Technology: Use risk management software to centralize and automate the tracking of your risk register for more efficient updates and reporting.
By following these steps, you can maintain a risk register that not only protects your organization from current threats but also adapts to future challenges.
Risk Register Examples
Having theoretical knowledge about what a risk register should include is one thing, but practical examples can crystallize the concept. Here are a couple of examples to illustrate how a risk register might look for different scenarios in a cybersecurity context.
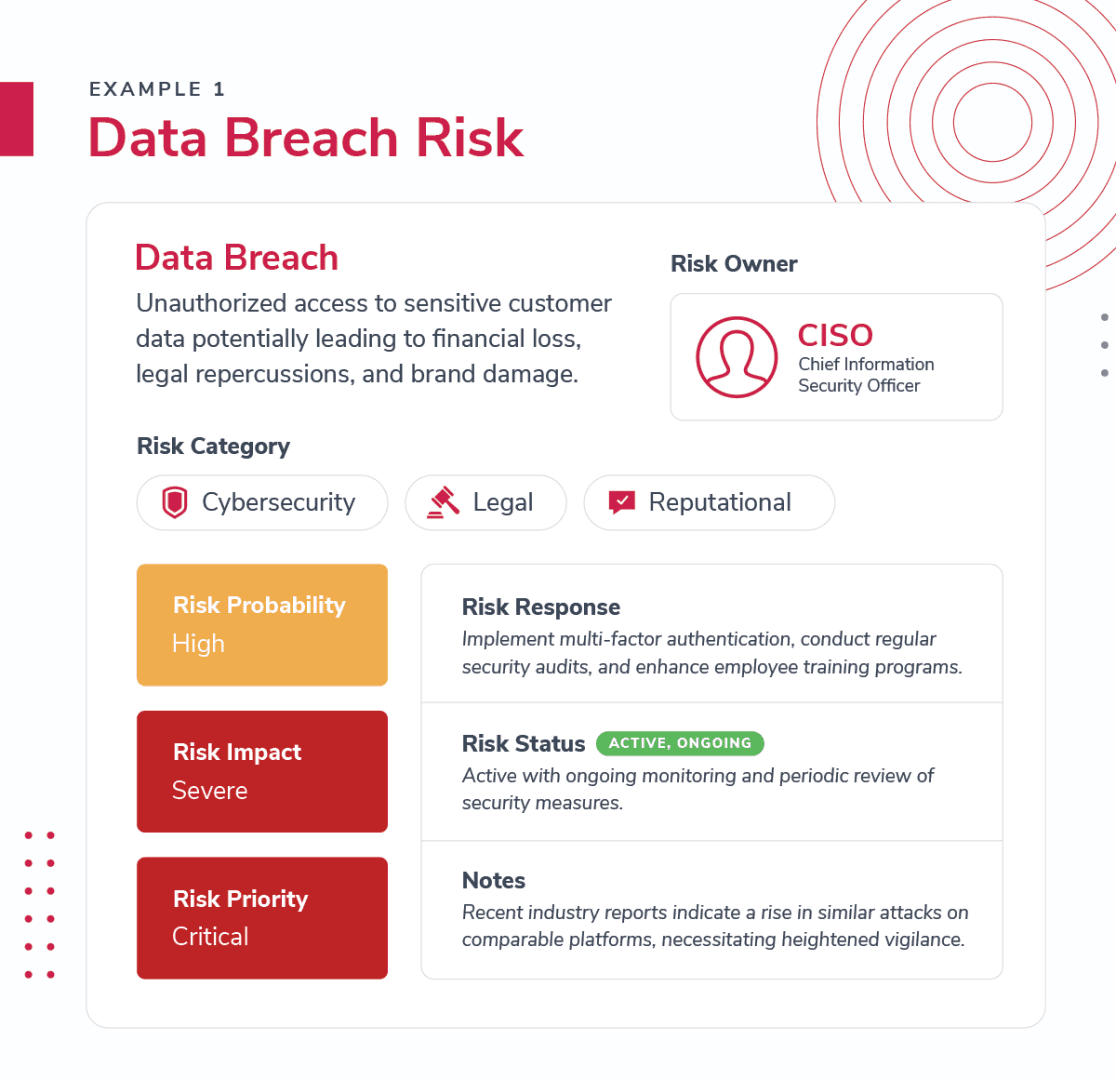
Risk Register Example 1: Data Breach Risk
Risk Identification: #001 - Data Breach
Risk Description: Unauthorized access to sensitive customer data potentially leading to financial loss, legal repercussions, and brand damage.
Risk Category: Cybersecurity, Legal, Reputational
Risk Ownership: Chief Information Security Officer (CISO)
Risk Probability: High, given the recent trend in targeted attacks within the industry.
Risk Impact: Severe, with possible customer churn and regulatory fines.
Risk Priority: Critical, due to the direct impact on customer trust and regulatory compliance.
Risk Response: Implement multi-factor authentication, conduct regular security audits, and enhance employee training programs.
Risk Status: Active, with ongoing monitoring and periodic review of security measures.
Notes: Recent industry reports indicate a rise in similar attacks on comparable platforms, necessitating heightened vigilance.
According to a recent study by the Ponemon Institute and IBM, the average cost of a data breach increased significantly, reaching $4.24 million last year. This figure highlights the growing financial impact and severity of data breaches on organizations worldwide.
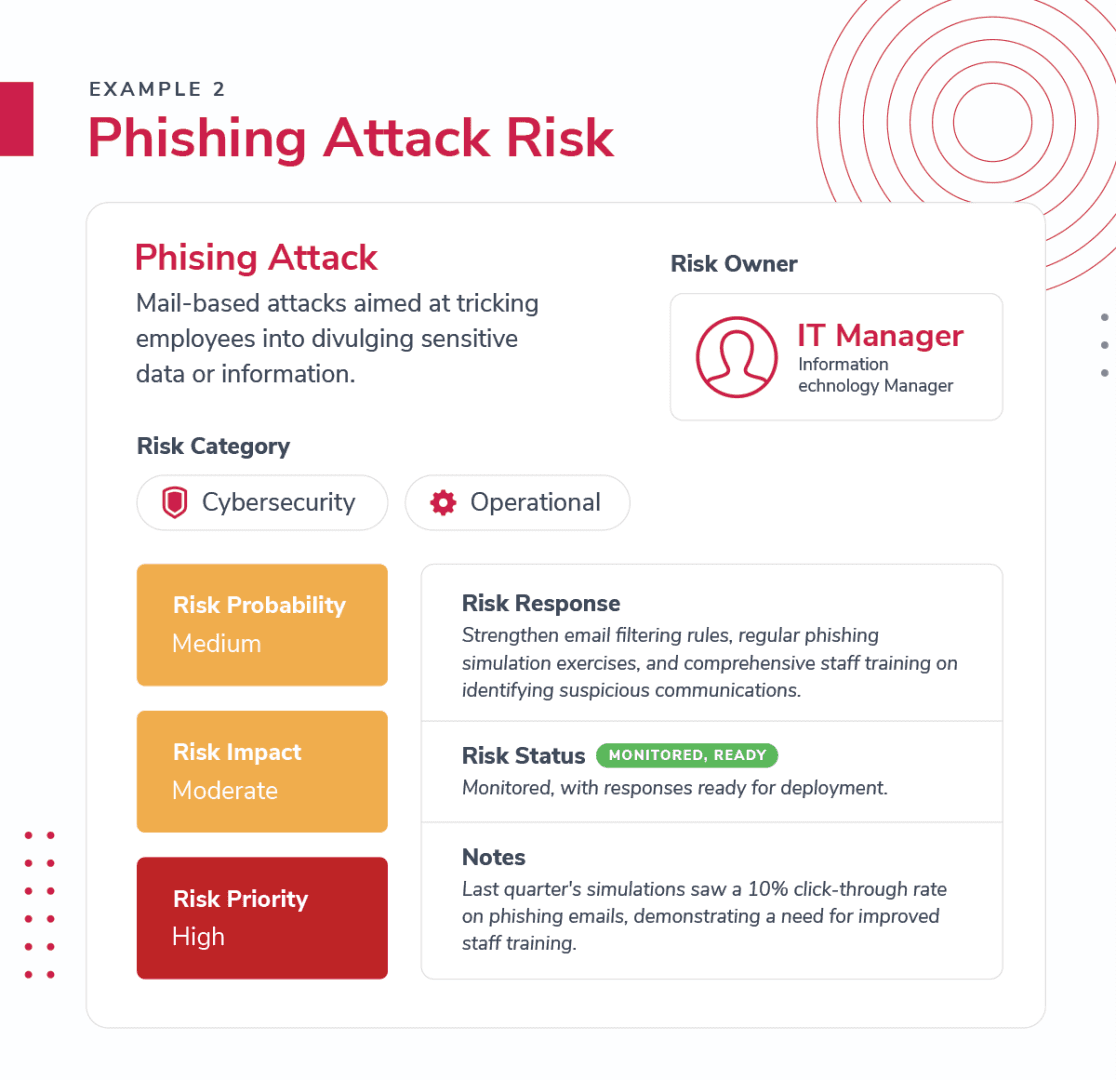
Risk Register Example 2: Phishing Attack Risk
Risk Identification: #002 - Phishing Attack
Risk Description: Email-based attacks aimed at tricking employees into divulging sensitive information.
Risk Category: Cybersecurity, Operational
Risk Ownership: IT Manager
Risk Probability: Medium, due to robust email filtering, but still possible through sophisticated tactics.
Risk Impact: Moderate, can lead to compromised internal systems and data leakage.
Risk Priority: High, as it targets human vulnerabilities, which are often the weakest link in security.
Risk Response: Strengthen email filtering rules, regular phishing simulation exercises, and comprehensive staff training on identifying suspicious communications.
Risk Status: Monitored, with responses ready for deployment.
Notes: Last quarter's simulations saw a 10% click-through rate on phishing emails, demonstrating a need for improved staff training.
These examples show how risks are logged with actionable insights, allowing for clarity and preparedness in an organization's cybersecurity approach. The details can be adapted based on the specific context and evolving cybersecurity landscape.
Essential Features of an Effective Risk Assessment Software
When considering what makes risk assessment software truly effective, it's crucial to focus on a few key features that enhance usability and accuracy:
User-Friendly Interface:
A top-tier software package should simplify the risk assessment process, allowing users to select options and execute actions with minimal effort. This ease of use ensures that teams can quickly adapt and integrate the software into their workflow.Comprehensive Reporting Capabilities:
Effective software should be equipped with the ability to generate detailed reports, such as a Statement of Applicability and a risk treatment plan. It should also allow for easy exporting, editing, and sharing of these documents, facilitating collaboration and communication across the organization and with external auditors.Consistent and Repeatable Assessments:
The software must provide a structured framework that can be applied uniformly over time. This consistency ensures that assessments are reliable, whether conducted annually or in response to changes in circumstances, thereby fostering continuous improvement.Accuracy and Error Reduction:
By minimizing human error, the software enhances the accuracy of risk assessments. Automation and streamlined processes play a critical role in reducing the likelihood of mistakes, ensuring that the data used for decision-making is precise and dependable.
By integrating these features, risk assessment software and GRC platforms like StandardFusion, can greatly improve an organization's ability to identify, evaluate, and mitigate potential risks effectively.
Final Thoughts
In wrapping up our journey through the world of information security risk registers, it's clear that this isn't just about managing risks, it's about empowering your organization to thrive in a digital era full of uncertainties.
With the strategies and insights you got from this guide, you're now better equipped to craft a risk register that not only identifies potential threats but also provides a clear roadmap for addressing them.
This guide is your ally in transforming the daunting task of cybersecurity into a structured, proactive mission.
As you put these practices into action, remember that your role is pivotal in steering your organization towards a safer, more resilient digital future.