Dec 11, 2024
Common GRC Risk Assessment Methodologies
Nearly two-thirds of organizations expect to increase their compliance budgets to keep up with requirements, especially with data breaches now taking an average of 277 days to detect and costing businesses $4.88 million on average.
But here's the good news: well-structured risk assessment methodologies can transform how organizations identify, evaluate, and manage their risks.
Let’s explore how risk methodologies strengthen GRC practices, helping to drive resilience and growth for your business.
Why Do Organizations Need a Risk Assessment Methodology?
Risk assessment methodologies are central to effective risk management, shaped by decades of hard-learned lessons – from financial scandals that led to SOX legislation to data breaches that redefined privacy standards.
Today, these assessments serve two vital roles:
Setting best practices to protect business operations and organizational assets:
Ensuring your business is compliant with both regulatory standards and internal procedures.
But as regulations continue to grow in complexity, compliance efforts are often pulling resources away from critical areas like threat detection and response, leaving organizations more vulnerable. Adding to the challenge, 71% of organizations report a shortage of cybersecurity skills, which has led to heavier workloads and unfilled roles, putting teams under further pressure.

Meanwhile, emerging technologies like generative AI and cryptocurrency bring new risks, with Gartner recently highlighting generative AI as the top trend set to impact compliance in the years ahead.
This is the current compliance environment businesses are confronting today: a fast-evolving regulatory landscape, stretched resources, and new risks that make strong risk management practices more vital than ever.
Understanding Risk Assessment vs. Risk Analysis
When diving into the world of risk management, it's crucial to distinguish between risk assessment and risk analysis, two pivotal terms that often create confusion.
Risk Assessment is the comprehensive process of identifying potential risks. It encompasses a broad, methodical approach to detect and evaluate the varying threats that a business or project might encounter. This step is vital as it sets the stage for a company's strategic planning and decision-making efforts.
Risk Analysis, on the other hand, is more granular. It involves a detailed examination of the identified risks, where each risk level is evaluated. This part of the process seeks to understand the probability and impact of each risk, providing a quantifiable perspective that supports informed decisions.
Both processes are essential components of the larger field of risk management, working hand in hand to ensure that potential issues are not only identified but also thoroughly understood and prioritized.
The Role of Risk Analysis in the Risk Assessment Process
Risk analysis is a crucial phase within the broader framework of risk assessment, serving as the bridge between risk identification and risk management. To truly appreciate its role, it helps to understand how it slots into the entire risk assessment journey, which unfolds through four interconnected steps.
Identifying Risks
This foundational step involves pinpointing all conceivable threats to your organization. While technological risks, particularly those involving cybersecurity, are prominent, your scope shouldn't be limited to just those. Engaging with employees and key stakeholders can reveal a diverse array of potential risks that might not be immediately apparent.
Evaluating Potential Impact
Once you’ve identified potential risks, the next step is to envisage their possible implications. This involves evaluating how these risks can manifest and what impact they might have on the organization.
Conducting Risk Analysis
This is where risk analysis steps into the spotlight. After drawing up a list of risks, each is scrutinized for its likelihood and potential severity. The analysis aims to determine not just the probability of each risk occurring, but also its critical importance. Complete elimination of risk is not the goal—since it's often impossible—but rather, forming a proportionate response. Risk analysis informs you about which risks require more immediate and robust actions.
Ongoing Review and Adjustment
The risk assessment process doesn’t end with analysis and initial action. Continuous review is essential to accommodate changes in circumstances or the emergence of new threats. Regular updates ensure that the organization always has a fresh perspective on risks and remains agile in managing them.
By intricately linking these stages together, risk analysis acts as a pivotal mechanism. It provides the intelligence and insight necessary to prioritize risks effectively, guiding organizations in deploying their resources where they are most needed. This ensures that risk management strategies are both strategic and dynamic, fostering resilience and adaptability.
How Regulations and Frameworks Guide Assessment Methods
Some regulations and frameworks go further than recommending risk assessments as a ‘best practice.’ Instead, they set out specific methods that organizations are expected–or legally required–to follow.
For example, frameworks like ISO 31000, NIST SP 800-30, and EU NIS2 Directive emphasize structured approaches to assessing risks. They may not dictate every detail, but they often specify key elements, such as the need for probability and impact assessments, stakeholder engagement, and regular reviews.
Some frameworks, like ISO 27001, require ongoing risk assessments and monitoring as part of their certification processes.
Others, like PCI DSS, mandate precise methods for evaluating risks to cardholder data. Non-compliance can result in legal action, including fines or even criminal proceedings.
Penalties for non-compliance have increased dramatically in recent years, surging by 31% in the first half of 2024. Fines issued for non-compliance with the CCPA are picking up pace, with Zoom currently holding the record for the largest fine at $85 million in 2021.
Common Risk Assessment Methodologies
Risk methodologies provide structured methods for identifying, evaluating, and managing risks. While the many methodologies vary, the fundamental aim of each is to turn threats and uncertainties into manageable challenges.
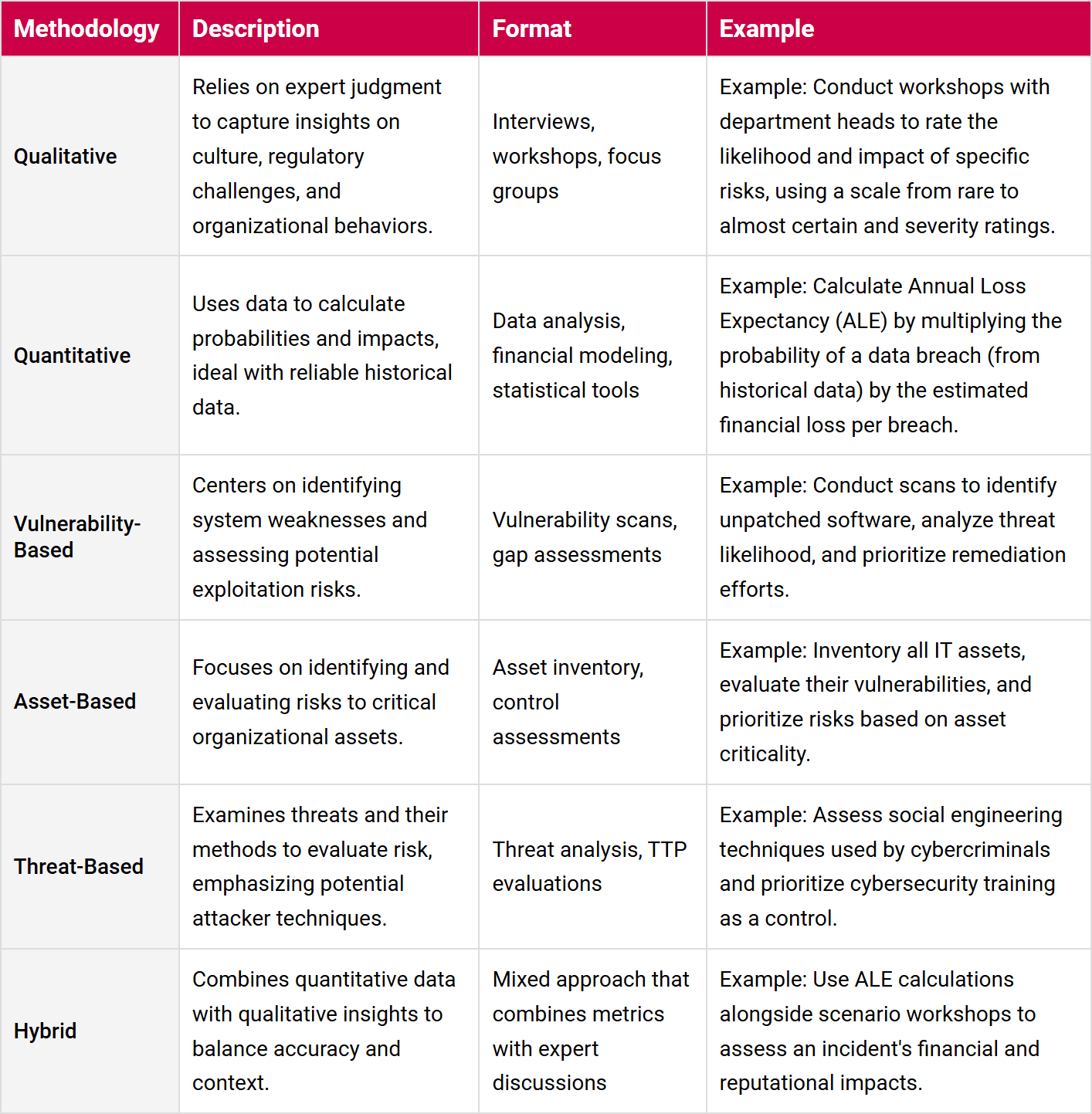
1. Qualitative Assessments
Qualitative methodologies tap into expert judgment, such as interviews, workshops, and focus groups. One of the most widely adopted qualitative frameworks is the 5x5 likelihood x impact matrix, inspired by standards such as those from the National Institute of Standards and Technology (NIST).
This matrix evaluates risks based on two dimensions: the likelihood of a risk event occurring and the severity of its impact. Each dimension is rated on a simple five-point scale, creating a matrix that helps prioritize risks. Qualitative assessments are extremely popular because they are easy to implement across teams and standardize risk assessments—an essential factor when establishing a unified GRC program.
A qualitative assessment calculation includes:
Likelihood (Probability of Occurrence)
Impact (Severity of Consequence)
Risk Score = Likelihood Value × Impact Value
Additionally, there are other types of qualitative risk assessments, including:
Residual Risk Score (Post-Control Evaluation)
Weighted Control Effectiveness (Comprehensive Mitigation)
Cost-Benefit Ratio (Efficiency Assessment)
Control Maturity Level (Operational Strength)
Probability-Impact with Vulnerability Score (Exposure Insight)
Qualitative risk assessments provide valuable insights into risk culture, regulatory challenges, and organizational behavior that the raw data of a quantitative approach might miss. This approach allows organizations flexibility to tailor risk assessment programs to enhance the overall process, provides a broader, more holistic view of risks and their implications, and ensures consistency across teams by adopting a common language for risk assessment while providing more straightforward decision making without specialized resources.
2. Quantitative Assessments
Quantitative methodologies rely on data to calculate probabilities and potential impacts. This works particularly well when a business can access reliable historical data or calculate specific financial impacts.
Here's what makes up a comprehensive quantitative assessment:
Annual Loss Expectancy (ALE) calculations combining probability and potential loss.
Return on Security Investment (ROSI) analysis to evaluate control effectiveness.
Asset valuation and depreciation considerations.
Probability analysis using historical data and industry statistics.
Cost-benefit analysis of different control options.
Time-to-recovery estimations and associated costs.
3. Vulnerability-Based Assessments
A vulnerability-based risk assessment focuses on identifying weaknesses or deficiencies in systems, processes, or environments that could be exploited by threats.
This approach begins by analyzing known vulnerabilities, such as outdated software, misconfigurations, or weak access controls, and evaluating the potential threats and impacts of exploitation. In the GRC, vulnerability-based assessments align closely with an organization's vulnerability management processes, ensuring that governance frameworks address critical gaps and compliance efforts mitigate security flaws.
This method enhances risk management by proactively addressing exposures but may overlook emerging or unknown risks, requiring complementary strategies for a comprehensive view.
4. Asset-Based Assessments
Asset-based risk assessments focus on evaluating risks by identifying and analyzing the organization's critical assets, such as systems, data, and infrastructure. This approach begins by an organization inventorying assets, categorizing them by value and criticality, and then assessing associated threats, their vulnerabilities, and the effectiveness of the organization’s existing controls.
In GRC, asset-based assessments help organizations prioritize risk mitigation efforts by highlighting the most impactful risks to high-value assets. This ensures that governance policies and compliance activities align with safeguarding core resources.
While effective for understanding technical and operational risks, this method may require complementary approaches to address broader organizational vulnerabilities, such as policy gaps or cultural issues.
5. Threat-Based Assessments
Threat-based risk assessments identify and analyze threats that could compromise an organization's operations, assets, or compliance obligations.
This approach evaluates the tactics, techniques, and procedures (TTPs) of potential threat actors—such as cybercriminals, insider threats, or natural disasters—and assesses the conditions under which these threats could materialize. Threat-based assessments provide a broader understanding of an organization’s risk posture by incorporating external and internal threat intelligence, enabling a more dynamic response to emerging risks.
Unlike asset-based assessments, which prioritize the protection of critical resources, threat-based methodologies may recommend strategies like enhanced cybersecurity training or third-party risk monitoring, ensuring governance and compliance efforts adapt to evolving threat landscapes.
6. Hybrid Methods
In many cases, it’s necessary to adopt a mixture of methodologies. This enables organizations to take advantage of hard data where available or appropriate while still capturing equally important qualitative insights that add much needed context to form the full picture.
This risk assessment approach enables organizations the flexibility and adaptability to develop a nuanced, actionable risk management strategy that grows with them.
Risk Assessment Method Comparison Table
Risk assessment methodologies play a pivotal role in refining and enhancing the risk assessment process. By providing a structured framework, they enable organizations to systematically evaluate potential threats.
Here are some key ways these methodologies improve the process:
Consistency and Efficiency
They offer a disciplined approach, which ensures consistency across assessments. This consistency not only speeds up the evaluation process but also minimizes errors that may arise from an ad-hoc approach.
Comprehensive Analysis
Methodologies guide teams to thoroughly explore all potential risks, ensuring no stone is left unturned. This comprehensive analysis assists in identifying both current and emergent threats, positioning the company to proactively address them.
Enhanced Decision-Making
By standardizing the assessment process, decision-makers receive clear, actionable insights. This leads to more informed decisions, as leaders can rely on coherent data-driven recommendations.
Better Resource Allocation
With enhanced clarity in the threat landscape, organizations can allocate resources more effectively and efficiently. This priority-driven approach ensures that efforts are concentrated on mitigating risks with the most significant potential impact.
Repeatable and Scalable
These methodologies provide a framework that can be repeatedly applied. As the organization grows, they can easily scale the process to accommodate a larger asset base or more complex digital ecosystems.
In conclusion, risk assessment methodologies transform a basic threat evaluation into a robust, insightful process, driving organizations towards better planning and management of potential risks.
The Importance of Choosing the Right Type of Risk Assessment
Different regulations and industry standards often dictate the type of risk assessments required, but organizations have flexibility in how they conduct them. The goal is to find methods that meet regulatory demands while emphasizing better business decisions for your organization. Let’s look at how risk assessments breakdown across sectors, industries, and different business requirements:
Key Considerations for Choosing a Risk Assessment Methodology
When selecting a risk assessment methodology, start by asking yourself what you hope to learn. Do you need concrete data, which would be best served by a quantitative risk assessment? Or are you looking for a broader, generalized understanding of enterprise risks, better suited to a qualitative approach?
Consider the scope of the assessment: Will it be limited to a specific department or span the entire extended enterprise? Additionally, think about how factors like industry, location, and company size impact your risk control requirements. Compliance and regulatory frameworks may necessitate specific techniques, so understanding legal requirements before conducting assessments is crucial.
Understanding Industry-Specific Risks
Every industry has its own set of risks to tackle. For example:
Financial services companies must be vigilant against fraud and money laundering.
Healthcare providers are responsible for protecting sensitive patient data.
Technology companies must anticipate rapidly emerging security threats while safeguarding intellectual property and securing digital processes and workloads.
Customizing Risk Assessment Strategies
Each methodology offers unique insights, tools, and perspectives, and the choice directly impacts how risks are identified, prioritized, and mitigated for each organization and industry. For example:
Financial services companies may combine SOX compliance with targeted financial risk assessments that suit their specific products.
Healthcare providers often integrate HIPAA data security requirements with HITRUST controls and CCPA or GDPR privacy regulations.
Technology companies pursuing SOC 2 certification might implement continuous control testing while aligning with ISO 27001 for risk management and GDPR/CPAA for data protection.
Leveraging Overlapping Frameworks
In some cases, frameworks and their requirements overlap, particularly for regulations intended to accomplish similar objectives, such as GDPR and CCPA. This is where dedicated GRC platforms become immensely useful. Rather than conducting separate assessments for each framework, you can leverage dedicated GRC platforms. GRC software like StandardFusion, helps organizations manage overlapping requirements. Rather than conducting separate assessments for each framework, you can leverage this software to assess controls and map them across multiple compliance requirements.
Key Takeaways
If you're involved in risk management, compliance, or security, you probably already know that using ad-hoc approaches in place of a holistic GRC tool simply won't cut it. Having a good risk assessment in place is a cornerstone of an effective GRC program, relying on the right methodology, consistent application, regular updates, and alignment with compliance goals.
Each element should connect with your business objectives and industry standards while staying flexible enough to scale with growth.
Key factors for success include:
Choosing a methodology that matches your organization’s needs and risk profile.
Seamlessly integrating assessments into existing processes and systems.
Keeping assessments current with regular updates and improvements.
Communicating clearly with stakeholders through reliable reporting.
Leveraging automation and standardized processes to enhance efficiency.
Building systems that scale as your business expands.
When executed correctly, risk assessment becomes a strategic asset, not just a compliance requirement. StandardFusion can help make that happen. We offer enterprise-grade software designed to help organizations develop effective risk management and compliance programs that fit their unique needs.
Ready to strengthen your risk assessment approach? Explore how StandardFusion can help you manage multiple compliance frameworks on one centralized platform.
Request a demo today to discover how we can streamline your GRC journey.







